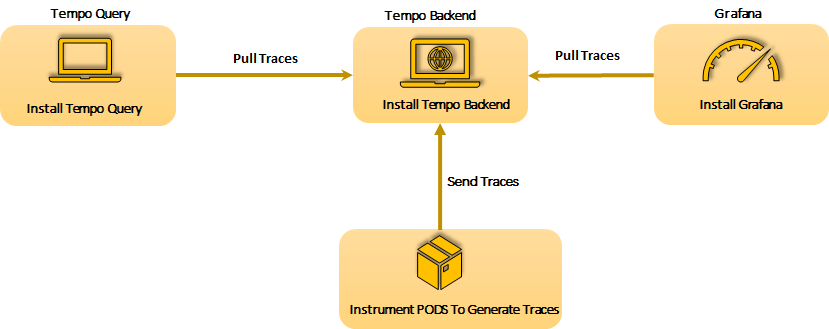
apiVersion: v1
kind: Template
metadata:
name: grafana
annotations:
"openshift.io/display-name": Grafana
description: |
A Visualization solution for Prometheus
iconClass: fa fa-cogs
tags: "dashboard, grafana"
parameters:
- name: APP_NAME
description: "Value for app label."
- name: NAME_SPACE
description: "The name of the namespace (openshift project)"
- name: IMAGE_GRAFANA
description: Grafana Docker image
required: true
value: "grafana/grafana:7.3.6"
- name: VOLUME_CAPACITY
displayName: Volume Capacity
description: Volume space available for data, e.g. 512Mi, 2Gi.
value: 20Gi
required: true
objects:
- apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: grafana-lib-pvc
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: "${VOLUME_CAPACITY}"
- apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: grafana-log-pvc
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: "${VOLUME_CAPACITY}"
- apiVersion: apps.openshift.io/v1
kind: DeploymentConfig
metadata:
labels:
app: ${APP_NAME}
name: ${APP_NAME}
namespace: "${NAME_SPACE}"
spec:
replicas: 1
selector:
app: ${APP_NAME}
template:
metadata:
labels:
app: ${APP_NAME}
name: grafana
spec:
containers:
- name: grafana
command:
- sh
args:
- -c
- /etc/grafana/grafana-prepare.sh ; exec /run.sh
image: ${IMAGE_GRAFANA}
imagePullPolicy: Always
ports:
- containerPort: 3000
name: grafana-http
protocol: TCP
livenessProbe:
httpGet:
path: /api/health
port: grafana-http
scheme: HTTP
initialDelaySeconds: 120
periodSeconds: 10
successThreshold: 1
failureThreshold: 3
timeoutSeconds: 1
readinessProbe:
failureThreshold: 3
httpGet:
path: /api/health
port: grafana-http
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
env:
- name: GF_AUTH_LDAP_ENABLED
value: 'true'
- name: GF_AUTH_LDAP_CONFIG_FILE
value: /var/lib/grafana/ldap.toml
- name: GF_INSTALL_PLUGINS
value: 'grafana-clock-panel'
- name: GRAFANA_BIND_PWD
valueFrom:
secretKeyRef:
name: app-secret
key: GRAFANA_BIND_PWD
resources:
limits:
cpu: "500m"
memory: "128Mi"
requests:
cpu: "250m"
memory: "64Mi"
volumeMounts:
- mountPath: /etc/grafana
name: grafana-etc-volume
- mountPath: /etc/grafana/provisioning/datasources
name: grafana-datasources-volume
- mountPath: /etc/grafana/provisioning/dashboards
name: grafana-dashboard-config-volume
- mountPath: /var/lib/grafana-dashboards
name: grafana-dashboards
- mountPath: /var/lib/grafana
name: grafana-lib-volume
- mountPath: /var/log/grafana
name: grafana-log-volume
volumes:
- name: grafana-datasources-volume
configMap:
defaultMode: 420
name: grafana-datasources
- name: grafana-dashboard-config-volume
configMap:
defaultMode: 420
name: grafana-dashboard-config
- name: grafana-etc-volume
configMap:
defaultMode: 0777
name: grafana
- name: grafana-dashboards
configMap:
defaultMode: 420
name: grafana-dashboards
- name: grafana-lib-volume
persistentVolumeClaim:
claimName: grafana-lib-pvc
- name: grafana-log-volume
persistentVolumeClaim:
claimName: grafana-log-pvc
- apiVersion: v1
kind: Service
name: grafana
metadata:
labels:
app: ${APP_NAME}
name: grafana
namespace: "${NAME_SPACE}"
spec:
ports:
- name: grafana
port: 3000
protocol: TCP
targetPort: grafana-http
selector:
app: grafana
- apiVersion: route.openshift.io/v1
kind: Route
metadata:
labels:
app: ${APP_NAME}
name: grafana
namespace: "${NAME_SPACE}"
spec:
to:
kind: Service
name: grafana
weight: 100
tls:
termination: edge
wildcardPolicy: None
- apiVersion: v1
kind: ConfigMap
metadata:
name: grafana
data:
grafana-prepare.sh: |
#!/bin/sh
set -eu
sed "s|<GRAFANA_BIND_PWD>|$GRAFANA_BIND_PWD|g" /etc/grafana/ldap_pl.toml > /var/lib/grafana/ldap.toml
grafana.ini: |
##################### Grafana Configuration Defaults #####################
#
# Do not modify this file in grafana installs
#
# possible values : production, development
app_mode = production
# instance name, defaults to HOSTNAME environment variable value or hostname if HOSTNAME var is empty
instance_name = ${HOSTNAME}
#################################### Paths ###############################
[paths]
# Path to where grafana can store temp files, sessions, and the sqlite3 db (if that is used)
#
data = data
#
# Directory where grafana can store logs
#
logs = data/log
#
# Directory where grafana will automatically scan and look for plugins
#
plugins = data/plugins
# Directory where grafana will look for provisioning files (Data Sources, Dashboards)
provisioning = provisioning
#################################### Server ##############################
[server]
# Protocol (http, https, socket)
protocol = http
# The ip address to bind to, empty will bind to all interfaces
http_addr =
# The http port to use
http_port = 3000
# The public facing domain name used to access grafana from a browser
domain = localhost
# Redirect to correct domain if host header does not match domain
# Prevents DNS rebinding attacks
enforce_domain = false
# The full public facing url
root_url = %(protocol)s://%(domain)s:%(http_port)s/
# Log web requests
router_logging = false
# the path relative working path
static_root_path = public
# enable gzip
enable_gzip = false
# https certs & key file
cert_file =
cert_key =
# Unix socket path
socket = /tmp/grafana.sock
#################################### Database ############################
[database]
# You can configure the database connection by specifying type, host, name, user and password
# as separate properties or as on string using the url property.
# Either "mysql", "postgres" or "sqlite3", it's your choice
type = sqlite3
host = 127.0.0.1:3306
name = grafana
user = root
# If the password contains # or ; you have to wrap it with triple quotes. Ex """#password;"""
password =
# Use either URL or the previous fields to configure the database
# Example: mysql://user:secret@host:port/database
url =
# Max conn setting default is 0 (mean not set)
max_idle_conn =
max_open_conn =
# For "postgres", use either "disable", "require" or "verify-full"
# For "mysql", use either "true", "false", or "skip-verify".
ssl_mode = disable
ca_cert_path =
client_key_path =
client_cert_path =
server_cert_name =
# For "sqlite3" only, path relative to data_path setting
path = grafana.db
#################################### Session #############################
[session]
# Either "memory", "file", "redis", "mysql", "postgres", "memcache", default is "file"
provider = file
# Provider config options
# memory: not have any config yet
# file: session dir path, is relative to grafana data_path
# redis: config like redis server e.g. `addr=127.0.0.1:6379,pool_size=100,db=grafana`
# postgres: user=a password=b host=localhost port=5432 dbname=c sslmode=disable
# mysql: go-sql-driver/mysql dsn config string, examples:
# `user:password@tcp(127.0.0.1:3306)/database_name`
# `user:password@unix(/var/run/mysqld/mysqld.sock)/database_name`
# memcache: 127.0.0.1:11211
provider_config = sessions
# Session cookie name
cookie_name = grafana_sess
# If you use session in https only, default is false
cookie_secure = false
# Session life time, default is 86400
session_life_time = 86400
gc_interval_time = 86400
#################################### Data proxy ###########################
[dataproxy]
# This enables data proxy logging, default is false
logging = false
#################################### Analytics ###########################
[analytics]
# Server reporting, sends usage counters to stats.grafana.org every 24 hours.
# No ip addresses are being tracked, only simple counters to track
# running instances, dashboard and error counts. It is very helpful to us.
# Change this option to false to disable reporting.
reporting_enabled = true
# Set to false to disable all checks to https://grafana.com
# for new versions (grafana itself and plugins), check is used
# in some UI views to notify that grafana or plugin update exists
# This option does not cause any auto updates, nor send any information
# only a GET request to https://grafana.com to get latest versions
check_for_updates = true
# Google Analytics universal tracking code, only enabled if you specify an id here
google_analytics_ua_id =
# Google Tag Manager ID, only enabled if you specify an id here
google_tag_manager_id =
#################################### Security ############################
[security]
# default admin user, created on startup
admin_user = admin
# default admin password, can be changed before first start of grafana, or in profile settings
admin_password = admin
# used for signing
secret_key = SW2YcwTIb9zpOOhoPsMm
# Auto-login remember days
login_remember_days = 7
cookie_username = grafana_user
cookie_remember_name = grafana_remember
# disable gravatar profile images
disable_gravatar = false
# data source proxy whitelist (ip_or_domain:port separated by spaces)
data_source_proxy_whitelist =
[snapshots]
# snapshot sharing options
external_enabled = true
external_snapshot_url = https://snapshots-origin.raintank.io
external_snapshot_name = Publish to snapshot.raintank.io
# remove expired snapshot
snapshot_remove_expired = true
# remove snapshots after 90 days
snapshot_TTL_days = 90
#################################### Users ####################################
[users]
# disable user signup / registration
allow_sign_up = false
# Allow non admin users to create organizations
allow_org_create = false
# Set to true to automatically assign new users to the default organization (id 1)
auto_assign_org = true
# Default role new users will be automatically assigned (if auto_assign_org above is set to true)
auto_assign_org_role = Viewer
# Require email validation before sign up completes
verify_email_enabled = false
# Background text for the user field on the login page
login_hint = email or username
# Default UI theme ("dark" or "light")
default_theme = dark
[auth]
# Set to true to disable (hide) the login form, useful if you use OAuth
disable_login_form = false
# Set to true to disable the signout link in the side menu. useful if you use auth.proxy
disable_signout_menu = false
#################################### Anonymous Auth ######################
[auth.anonymous]
# enable anonymous access
enabled = false
# specify organization name that should be used for unauthenticated users
org_name = Main Org.
# specify role for unauthenticated users
org_role = Viewer
#################################### Github Auth #########################
[auth.github]
enabled = false
allow_sign_up = true
client_id = some_id
client_secret = some_secret
scopes = user:email
auth_url = https://github.com/login/oauth/authorize
token_url = https://github.com/login/oauth/access_token
api_url = https://api.github.com/user
team_ids =
allowed_organizations =
#################################### Google Auth #########################
[auth.google]
enabled = false
allow_sign_up = true
client_id = some_client_id
client_secret = some_client_secret
scopes = https://www.googleapis.com/auth/userinfo.profile https://www.googleapis.com/auth/userinfo.email
auth_url = https://accounts.google.com/o/oauth2/auth
token_url = https://accounts.google.com/o/oauth2/token
api_url = https://www.googleapis.com/oauth2/v1/userinfo
allowed_domains =
hosted_domain =
#################################### Grafana.com Auth ####################
# legacy key names (so they work in env variables)
[auth.grafananet]
enabled = false
allow_sign_up = true
client_id = some_id
client_secret = some_secret
scopes = user:email
allowed_organizations =
[auth.grafana_com]
enabled = false
allow_sign_up = true
client_id = some_id
client_secret = some_secret
scopes = user:email
allowed_organizations =
#################################### Generic OAuth #######################
[auth.generic_oauth]
name = OAuth
enabled = false
allow_sign_up = true
client_id = some_id
client_secret = some_secret
scopes = user:email
auth_url =
token_url =
api_url =
team_ids =
allowed_organizations =
#################################### Basic Auth ##########################
[auth.basic]
enabled = true
#################################### Auth Proxy ##########################
[auth.proxy]
enabled = false
header_name = X-WEBAUTH-USER
header_property = username
auto_sign_up = true
ldap_sync_ttl = 60
whitelist =
#################################### Auth LDAP ###########################
[auth.ldap]
enabled = true
config_file = /var/lib/grafana/ldap.toml
# Allow sign up should almost always be true (default) to allow new Grafana users to be created (if LDAP authentication is ok). If set to
# false only pre-existing Grafana users will be able to login (if LDAP authentication is ok).
allow_sign_up = true
#################################### SMTP / Emailing #####################
[smtp]
enabled = true
host = smtp-host.org.com:25 ## CHANGE THIS
user =
# If the password contains # or ; you have to wrap it with trippel quotes. Ex """#password;"""
password =
cert_file =
key_file =
skip_verify = true
from_address = [email protected]
from_name = Grafana
[emails]
welcome_email_on_sign_up = false
templates_pattern = emails/*.html
#################################### Logging ##########################
[log]
# Either "console", "file", "syslog". Default is console and file
# Use space to separate multiple modes, e.g. "console file"
mode = console file
# Either "debug", "info", "warn", "error", "critical", default is "info"
level = info
# optional settings to set different levels for specific loggers. Ex filters = sqlstore:debug
filters =
# For "console" mode only
[log.console]
level =
# log line format, valid options are text, console and json
format = console
# For "file" mode only
[log.file]
level =
# log line format, valid options are text, console and json
format = text
# This enables automated log rotate(switch of following options), default is true
log_rotate = true
# Max line number of single file, default is 1000000
max_lines = 1000000
# Max size shift of single file, default is 28 means 1 << 28, 256MB
max_size_shift = 28
# Segment log daily, default is true
daily_rotate = true
# Expired days of log file(delete after max days), default is 7
max_days = 7
[log.syslog]
level =
# log line format, valid options are text, console and json
format = text
# Syslog network type and address. This can be udp, tcp, or unix. If left blank, the default unix endpoints will be used.
network =
address =
# Syslog facility. user, daemon and local0 through local7 are valid.
facility =
# Syslog tag. By default, the process' argv[0] is used.
tag =
#################################### AMQP Event Publisher ################
[event_publisher]
enabled = false
rabbitmq_url = amqp://localhost/
exchange = grafana_events
#################################### Dashboard JSON files ################
[dashboards.json]
enabled = false
path = /var/lib/grafana/dashboards
#################################### Usage Quotas ########################
[quota]
enabled = false
#### set quotas to -1 to make unlimited. ####
# limit number of users per Org.
org_user = 10
# limit number of dashboards per Org.
org_dashboard = 100
# limit number of data_sources per Org.
org_data_source = 10
# limit number of api_keys per Org.
org_api_key = 10
# limit number of orgs a user can create.
user_org = 10
# Global limit of users.
global_user = -1
# global limit of orgs.
global_org = -1
# global limit of dashboards
global_dashboard = -1
# global limit of api_keys
global_api_key = -1
# global limit on number of logged in users.
global_session = -1
#################################### Alerting ############################
[alerting]
# Disable alerting engine & UI features
enabled = true
# Makes it possible to turn off alert rule execution but alerting UI is visible
execute_alerts = true
#################################### Internal Grafana Metrics ############
# Metrics available at HTTP API Url /api/metrics
[metrics]
enabled = true
interval_seconds = 10
# Send internal Grafana metrics to graphite
[metrics.graphite]
# Enable by setting the address setting (ex localhost:2003)
address =
prefix = prod.grafana.%(instance_name)s.
[grafana_net]
url = https://grafana.com
[grafana_com]
url = https://grafana.com
#################################### External Image Storage ##############
[external_image_storage]
# You can choose between (s3, webdav)
provider =
[external_image_storage.s3]
bucket_url =
access_key =
secret_key =
[external_image_storage.webdav]
url =
username =
password =
public_url =
ldap_pl.toml: |
# https://grafana.com/docs/grafana/latest/auth/ldap/
[[servers]]
# Ldap server host (specify multiple hosts space separated)
host = "ad-ldap.org.com" ### CHANGE THIS
# Default port is 389 or 636 if use_ssl = true
port = 389
# Set to true if LDAP server supports TLS
use_ssl = false
# Set to true if connect LDAP server with STARTTLS pattern (create connection in insecure, then upgrade to secure connection with TLS)
start_tls = false
# set to true if you want to skip SSL cert validation
ssl_skip_verify = false
# set to the path to your root CA certificate or leave unset to use system defaults
# root_ca_cert = "/path/to/certificate.crt"
# Authentication against LDAP servers requiring client certificates
# client_cert = "/path/to/client.crt"
# client_key = "/path/to/client.key"
# Search user bind dn
bind_dn = "cn=app_grafana,cn=users,dc=ms,dc=ds,dc=org,dc=com" ## change app_grafana to what ever valid service user
# Search user bind password
# If the password contains # or ; you have to wrap it with triple quotes. Ex """#password;"""
bind_password = '<GRAFANA_BIND_PWD>'
# User search filter, for example "(cn=%s)" or "(sAMAccountName=%s)" or "(uid=%s)"
# Allow login from email or username, example "(|(sAMAccountName=%s)(userPrincipalName=%s))"
# search_filter = "(&(objectClass=user)(objectClass=top)(cn=%s))"
search_filter = "(cn=%s)"
# An array of base dns to search through
search_base_dns = ["dc=ms,dc=ds,dc=org,dc=com"]
# group_search_filter = "(&(objectClass=posixGroup)(memberUid=%s))"
# group_search_filter_user_attribute = "distinguishedName"
# group_search_base_dns = ["ou=groups,dc=grafana,dc=org"]
# Specify names of the LDAP attributes your LDAP uses
[servers.attributes]
name = "givenName"
surname = "sn"
username = "cn"
member_of = "memberOf"
email = "mail"
[[servers.group_mappings]]
group_dn = "CN=APP_infra_admin,CN=Users,DC=ms,DC=ds,DC=org,DC=com" ## CHANGE APP_infra_admin to valid group name
org_role = "Admin"
# The Grafana organization database id, optional, if left out the default org (id 1) will be used
# org_id = 1
[[servers.group_mappings]]
#group_dn = "cn=users,dc=grafana,dc=org"
#org_role = "Editor"
[[servers.group_mappings]]
# If you want to match all (or no ldap groups) then you can use wildcard
group_dn = "*"
org_role = "Viewer"
- apiVersion: v1
kind: ConfigMap
metadata:
name: grafana-datasources
data:
prometheus.yml: |
# config file version
apiVersion: 1
# list of datasources to insert/update depending
# whats available in the database
datasources:
# <string, required> name of the datasource. Required
- name: DS-Prometheus
# <string, required> datasource type. Required
type: prometheus
# <string, required> access mode. direct or proxy. Required
access: proxy
# <int> org id. will default to orgId 1 if not specified
orgId: 1
# <string> url
url: http://prometheus:9090
version: 1
# <bool> mark as default datasource. Max one per org
isDefault: true
# <bool> allow users to edit datasources from the UI.
editable: true
- apiVersion: v1
kind: ConfigMap
metadata:
name: grafana-dashboard-config
data:
openshift-metrics-dashboard.yaml: |
apiVersion: 1
providers:
- name: 'default'
orgId: 1
folder: ''
type: file
disableDeletion: false
editable: false
options:
path: /var/lib/grafana-dashboards
- apiVersion: v1
kind: ConfigMap
metadata:
name: grafana-dashboards
data:
openshift-metrics-dashboard.json: |
{
}