Better API Security with Automation
2 likes645 views
API security needs to be thought with agility and collaboration in mind. In this presentation, we explain why API security must be automated: explosion of endpoints, continuous change, human errors and early involvement of security teams in API dev process.
1 of 33
Downloaded 34 times































Ad
Recommended
42crunch-API-security-workshop



42crunch-API-security-workshop42Crunch If you ask about API security, you will be most likely be told about OAuth2, may be OpenID Connect and of course TLS.
But in order to properly secure APIs, you will have to address many other aspects. This presentation cover key concepts related to API Security, as well as practical tools/solutions to address the overall issue, such as:
- Transport and message encryption.
- Digital Signatures
- Auditing and non-repudiation
- SecDevOps and security as code
- Coding best practices and how to enforce them
- Infrastructure Best Practices
SecDevOps for API Security



SecDevOps for API Security42Crunch As the pace at which APIs are created, proper security requires automation. This presentation introduces top OWASP issues which are occurring today and a series of steps to better protect our APIs.
Advanced API Security Patterns



Advanced API Security Patterns42Crunch While TLS and OAuth are widely used today, they are not always well-used and in many cases they are not enough. In this presentation, we introduce all aspects of security to consider as well as the OpenAPI security extensions which can be leveraged to better express the contract between the consumer and the provider.
APIDays Paris Security Workshop



APIDays Paris Security Workshop42Crunch Slides from my workshop in Paris, with practical tips on Security at the technical and organisational levels.
API Security: the full story



API Security: the full story42Crunch In this presentation, we explain why OAuth and SSL are not enough when it comes to API Security, and that you should also think about addressing other aspects such as confidentiality, integrity, audit or compliance requirements. We expose the tactics to address each of those aspects, and a set of recommendations to apply immediately to your APIs development.
Guidelines to protect your APIs from threats



Guidelines to protect your APIs from threatsIsabelle Mauny 1) The document discusses securing APIs and provides guidance on a layered approach including application level security, guiding principles like zero trust architecture, and protecting against specific API threats outlined in the OWASP API Security Top 10.
2) It summarizes real stories of API vulnerabilities from companies like Uber, Facebook, and Equifax and provides mitigations for each.
3) The key recommendations are to incorporate API security at design time, conduct security testing of APIs, and automate security through practices like DevSecOps.
Why you need API Security Automation



Why you need API Security Automation42Crunch Ever faster agile development and a wide gap across development and security teams are 2 of the main reasons you want to entirely automate all aspects of API security: code scans, infra scans, security testing, automatic policies deployment and deployment of lightweight, secure enforcement points (PEPs). Let's shift left!
Presentation given at APIDays Paris in Jan 2018.
API Security in a Microservices World



API Security in a Microservices World42Crunch A microservice architecture brings new challenges to API Security and careful design needs to be applied at operations and development level to ensure corporate data is properly protected from unwanted access.
In this session we explain what API security encompasses, why API security needs to be considered as early as possible in the lifecycle of the microservices, how known standards such as OAuth and OpenID Connect can be leveraged to authenticate and authorize access to microservices and give practical examples and recommendations for the design and deployment of microservice architectures.
OWASP API Security Top 10 Examples



OWASP API Security Top 10 Examples42Crunch The document discusses the OWASP API Security Top 10 project which aims to raise awareness of common API vulnerabilities. It highlights some frequent issues like input validation problems, insecure configurations, and data/exception leakage. The document also demonstrates examples of these vulnerabilities using a vulnerable demo API called Pixi.
API Security Guidelines: Beyond SSL and OAuth.



API Security Guidelines: Beyond SSL and OAuth.Isabelle Mauny This document provides guidelines for proper API security. It discusses evolving API security from established perimeters to blurry perimeters. It emphasizes that API security needs to consider authentication, authorization, integrity, confidentiality, availability, audit, and other aspects. It recommends implementing governance, evaluating coverage, establishing risk-based policies, and automating security through the full development cycle.
Top API Security Issues Found During POCs



Top API Security Issues Found During POCs42Crunch WATCH WEBINAR: https://youtu.be/LLVOouA4pbs
Over the past 6 months, we have discovered many similarities across APIs from companies from very different industries. "This is an eye opener" is the most recurring comment from our prospects. We thought it would be worth sharing our findings in this webinar.
Through a mix of slides and demos, we will describe the top 5 issues our security audit reports, what they are and why they matter, including:
- Potentials attacks linked to each issue
- How they can be remediated
- Example request/response and reports
The Dev, Sec and Ops of API Security - API World



The Dev, Sec and Ops of API Security - API World42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Five Principles to API Security



Five Principles to API SecurityIsabelle Mauny This document discusses the need for API security as APIs increasingly expose enterprise data and processes both internally and externally. It notes that while APIs may seem invisible without a GUI, they can be easily discovered and are vulnerable to the same threats as web applications if not properly secured. The document advocates for a holistic approach to API security that considers authentication, authorization, integrity, confidentiality and other aspects. It also emphasizes that the right security measures depend on the type of API and calls for collaboration between operations, development, security and business teams to implement proper API security.
Applying API Security at Scale



Applying API Security at ScaleNordic APIs By Isabelle Mauny, Chief Product Officer & Co-Founder at 42Crunch
With the crazy rate at which APIs are developed, enterprises face a delicate situation to secure them. Data validation, input sanitization, security testing are tasks that require a lot of attention and time. When done very late in the API lifecycle, results are usually disastrous. API Security must be fully part of the API lifecycle, as transparent as possible, preventing developers from introducing vulnerabilities early on. A bug discovered in production can cost up to 30 times more effort to solve. Security vulnerabilities are no different.
APISecurity_OWASP_MitigationGuide 



APISecurity_OWASP_MitigationGuide Isabelle Mauny Presentation from the OWASP 20th Anniversary conference. An overview of API Security issues and associated top 10 and how to address them.
Protecting Microservices APIs with 42Crunch API Firewall



Protecting Microservices APIs with 42Crunch API Firewall42Crunch In loosely coupled architectures, we must put in place application level security, should it be for client traffic (North-South) or intra-microservices traffic (East-West).
In this webinar, we show you how the 42Crunch API firewall can be used to put API threat protection in place automatically, as early as design time.
We’ll use a mix of slides and demos to present:
(1) The various elements of security to consider in order to cover the full API security scope (infrastructure vs application level security)
(2) Which threat protections must be put in place in a microservices architecture, and where
(3) How to leverage OpenAPI (aka Swagger) to configure threat protection from design time
(4) How to automate threat protection deployment
OWASP API Security TOP 10 - 2019



OWASP API Security TOP 10 - 2019Miguel Angel Falcón Muñoz The document summarizes the OWASP API Security Top 10 - 2019, which outlines the top 10 most critical API security risks. It includes an introduction to the OWASP API Security Top 10 project, release notes on the first edition, a description of the risk rating methodology used, and summaries of the top 10 risks which are: 1) Broken Object Level Authorization, 2) Broken Authentication, 3) Excessive Data Exposure, 4) Lack of Resources & Rate Limiting, 5) Broken Function Level Authorization.
OWASP API Security Top 10 - Austin DevSecOps Days



OWASP API Security Top 10 - Austin DevSecOps Days42Crunch In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
The Dev, Sec and Ops of API Security - NordicAPIs



The Dev, Sec and Ops of API Security - NordicAPIs42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
OWASP API Security Top 10 - API World



OWASP API Security Top 10 - API World42Crunch This document outlines the OWASP API Security Top 10 project which identifies the top 10 risks associated with modern application programming interfaces (APIs). It describes each of the top 10 risks, including broken authentication, excessive data exposure, lack of resources and rate limiting, and insufficient logging and monitoring. For each risk, it provides real-world examples of APIs that have been exploited and mitigation strategies are proposed. Additional resources for the project are listed at the end.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
WEBINAR: OWASP API Security Top 10



WEBINAR: OWASP API Security Top 1042Crunch WATCH WEBINAR: https://youtu.be/zTkv_9ChVPY
In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Injecting Security into vulnerable web apps at Runtime



Injecting Security into vulnerable web apps at RuntimeAjin Abraham Web Application Security is not hard, but it’s easy to get it wrong as writing secure code is not easy as preaching. So to overcome incidents happening from such unforeseen events, organisations tend to rely on Web Application Firewalls or WAFs. Web Application Firewalls have been in the industry for a long time. Every one of them either work outside or around the web applications and act by intercepting the HTTP request coming to the web server, then take a decision to allow or block the request based on traditional signature checks. They are never aware of what is happening inside the application like how the user input is getting interpreted, Is the application/server under heavy load?, Is the attacker exfiltrating data by exploiting an SQLi that WAF couldn’t detect? etc. The strength of traditional WAF depends on manual or predefined rules/signature. As a result, they have the limitation that they will get bypassed if a payload is not present in their signature list. In the occurrence of a zero day, a WAF in most cases won’t be able to prevent an attack as they don’t know the signature of the exploit yet.
In this talk I will share my research outcomes on implementing a runtime application patching algorithm on an insecurely coded application to make it secure against code injection vulnerabilities and other logical issues related to web applications. I will introduce the next generation web application defending technology dubbed as Runtime Application Self Protection (RASP) that works by understanding your application to defend against web attacks by working inside the web application. RASP relies on Runtime Patching to inject security into web apps implicitly without introducing additional code changes. The root cause of all the code injection vulnerabilities is that the language interpreter cannot distinguish between data and code. The proposed solution will detect code context breakout to effectively detect and prevent code injections with the help of runtime hooking and patching at framework api or language api level. The research focuses mainly on detecting and preventing vulnerabilities like SQL Injection, Cross Site Scripting, Remote Command Execution, HTTP Verb Tampering, Header Injection, File Upload Bypass, Path Traversal etc and other application security challenges like Session Hijacking, Credential Stuffing and Layer 7 DDoS etc. This research is carried out by implementing a RASP module to a vulnerable web application written in python using tornado framework with sqlite backend.
API Security - OWASP top 10 for APIs + tips for pentesters



API Security - OWASP top 10 for APIs + tips for pentestersInon Shkedy The document discusses modern application security issues related to APIs. It begins with an overview of common API security risks like SQL injection, XSS, and CSRF. It then focuses on how application security has changed with the transition to modern architectures that are API-focused, use cloud infrastructure, and follow DevOps practices. Key changes discussed include less abstraction layers, clients handling more responsibility, and APIs exposing more data and endpoints directly. The document also summarizes the OWASP API security project and proposed API security top 10 risks. Real attack examples are provided to illustrate broken authorization and authentication vulnerabilities.
Checkmarx meetup API Security - API Security in depth - Inon Shkedy



Checkmarx meetup API Security - API Security in depth - Inon ShkedyAdar Weidman The document discusses modern application security challenges with APIs, provides real world examples of API vulnerabilities, and discusses solutions. It begins by introducing common API security issues like object level authorization (BOLA) and function level authorization (BFLA). It then details two real attacks - one on a food delivery app that allowed account takeover via phone number verification, and one on a social network that allowed email updating due to inconsistent authorization. The document advocates for proper authorization mechanisms and expanding the attack surface to find vulnerabilities.
Injecting Security into Web apps at Runtime Whitepaper



Injecting Security into Web apps at Runtime WhitepaperAjin Abraham This document discusses a method called Runtime Application Self Defence (RASP) to securely inject protections into web applications at runtime without requiring code changes. RASP works by hooking into critical APIs, learning an application's behavior to generate rules, and then monitoring for context breaks to prevent attacks like SQL injection and cross-site scripting. The key advantages of RASP over traditional WAFs are that it operates from within the application so it understands the application context and can prevent zero-day attacks.
OWASP Top 10 2017 rc1 - The Ten Most Critical Web Application Security Risks



OWASP Top 10 2017 rc1 - The Ten Most Critical Web Application Security RisksAndre Van Klaveren A presentation of the OWASP Top 10 2017 release candidate, expected to be finalized in summer 2017. Presented at the St. Louis CYBER meetup on Wednesday, June 7, 2017.
OWASP Top 10 - 2017 Top 10 web application security risks



OWASP Top 10 - 2017 Top 10 web application security risksKun-Da Wu The OWASP team recently released the 2017 revised version of the ten most critical web application security risks. This presentation brief the OWASP Top 10 - 2017 for you to learn more about these important security issues.
Owasp top 10 web application security risks 2017



Owasp top 10 web application security risks 2017Sampath Bhargav Pinnam The document outlines the OWASP Top 10 application security risks for 2017. It discusses the top 10 risks which are injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, use of vulnerable components, and insufficient logging and monitoring. It provides details on each risk such as examples and how attackers can exploit them. The document also discusses OWASP's goal of raising awareness of application security needs and best practices for developers and organizations.
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxazida3 The document discusses validating all inputs to prevent cross-site scripting (XSS) attacks. It introduces the OWASP HTML Sanitizer Project, which is a Java library that sanitizes HTML to allow untrusted user input to be safely embedded in web pages. The sanitizer removes malicious code while keeping desired markup, through a policy-based approach. Sample usages demonstrated validate specific elements like images and links. The project aims to protect against XSS while allowing third-party content through a tested, securely-designed library.
More Related Content
What's hot (20)
OWASP API Security Top 10 Examples



OWASP API Security Top 10 Examples42Crunch The document discusses the OWASP API Security Top 10 project which aims to raise awareness of common API vulnerabilities. It highlights some frequent issues like input validation problems, insecure configurations, and data/exception leakage. The document also demonstrates examples of these vulnerabilities using a vulnerable demo API called Pixi.
API Security Guidelines: Beyond SSL and OAuth.



API Security Guidelines: Beyond SSL and OAuth.Isabelle Mauny This document provides guidelines for proper API security. It discusses evolving API security from established perimeters to blurry perimeters. It emphasizes that API security needs to consider authentication, authorization, integrity, confidentiality, availability, audit, and other aspects. It recommends implementing governance, evaluating coverage, establishing risk-based policies, and automating security through the full development cycle.
Top API Security Issues Found During POCs



Top API Security Issues Found During POCs42Crunch WATCH WEBINAR: https://youtu.be/LLVOouA4pbs
Over the past 6 months, we have discovered many similarities across APIs from companies from very different industries. "This is an eye opener" is the most recurring comment from our prospects. We thought it would be worth sharing our findings in this webinar.
Through a mix of slides and demos, we will describe the top 5 issues our security audit reports, what they are and why they matter, including:
- Potentials attacks linked to each issue
- How they can be remediated
- Example request/response and reports
The Dev, Sec and Ops of API Security - API World



The Dev, Sec and Ops of API Security - API World42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Five Principles to API Security



Five Principles to API SecurityIsabelle Mauny This document discusses the need for API security as APIs increasingly expose enterprise data and processes both internally and externally. It notes that while APIs may seem invisible without a GUI, they can be easily discovered and are vulnerable to the same threats as web applications if not properly secured. The document advocates for a holistic approach to API security that considers authentication, authorization, integrity, confidentiality and other aspects. It also emphasizes that the right security measures depend on the type of API and calls for collaboration between operations, development, security and business teams to implement proper API security.
Applying API Security at Scale



Applying API Security at ScaleNordic APIs By Isabelle Mauny, Chief Product Officer & Co-Founder at 42Crunch
With the crazy rate at which APIs are developed, enterprises face a delicate situation to secure them. Data validation, input sanitization, security testing are tasks that require a lot of attention and time. When done very late in the API lifecycle, results are usually disastrous. API Security must be fully part of the API lifecycle, as transparent as possible, preventing developers from introducing vulnerabilities early on. A bug discovered in production can cost up to 30 times more effort to solve. Security vulnerabilities are no different.
APISecurity_OWASP_MitigationGuide 



APISecurity_OWASP_MitigationGuide Isabelle Mauny Presentation from the OWASP 20th Anniversary conference. An overview of API Security issues and associated top 10 and how to address them.
Protecting Microservices APIs with 42Crunch API Firewall



Protecting Microservices APIs with 42Crunch API Firewall42Crunch In loosely coupled architectures, we must put in place application level security, should it be for client traffic (North-South) or intra-microservices traffic (East-West).
In this webinar, we show you how the 42Crunch API firewall can be used to put API threat protection in place automatically, as early as design time.
We’ll use a mix of slides and demos to present:
(1) The various elements of security to consider in order to cover the full API security scope (infrastructure vs application level security)
(2) Which threat protections must be put in place in a microservices architecture, and where
(3) How to leverage OpenAPI (aka Swagger) to configure threat protection from design time
(4) How to automate threat protection deployment
OWASP API Security TOP 10 - 2019



OWASP API Security TOP 10 - 2019Miguel Angel Falcón Muñoz The document summarizes the OWASP API Security Top 10 - 2019, which outlines the top 10 most critical API security risks. It includes an introduction to the OWASP API Security Top 10 project, release notes on the first edition, a description of the risk rating methodology used, and summaries of the top 10 risks which are: 1) Broken Object Level Authorization, 2) Broken Authentication, 3) Excessive Data Exposure, 4) Lack of Resources & Rate Limiting, 5) Broken Function Level Authorization.
OWASP API Security Top 10 - Austin DevSecOps Days



OWASP API Security Top 10 - Austin DevSecOps Days42Crunch In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
The Dev, Sec and Ops of API Security - NordicAPIs



The Dev, Sec and Ops of API Security - NordicAPIs42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
OWASP API Security Top 10 - API World



OWASP API Security Top 10 - API World42Crunch This document outlines the OWASP API Security Top 10 project which identifies the top 10 risks associated with modern application programming interfaces (APIs). It describes each of the top 10 risks, including broken authentication, excessive data exposure, lack of resources and rate limiting, and insufficient logging and monitoring. For each risk, it provides real-world examples of APIs that have been exploited and mitigation strategies are proposed. Additional resources for the project are listed at the end.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
WEBINAR: OWASP API Security Top 10



WEBINAR: OWASP API Security Top 1042Crunch WATCH WEBINAR: https://youtu.be/zTkv_9ChVPY
In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Injecting Security into vulnerable web apps at Runtime



Injecting Security into vulnerable web apps at RuntimeAjin Abraham Web Application Security is not hard, but it’s easy to get it wrong as writing secure code is not easy as preaching. So to overcome incidents happening from such unforeseen events, organisations tend to rely on Web Application Firewalls or WAFs. Web Application Firewalls have been in the industry for a long time. Every one of them either work outside or around the web applications and act by intercepting the HTTP request coming to the web server, then take a decision to allow or block the request based on traditional signature checks. They are never aware of what is happening inside the application like how the user input is getting interpreted, Is the application/server under heavy load?, Is the attacker exfiltrating data by exploiting an SQLi that WAF couldn’t detect? etc. The strength of traditional WAF depends on manual or predefined rules/signature. As a result, they have the limitation that they will get bypassed if a payload is not present in their signature list. In the occurrence of a zero day, a WAF in most cases won’t be able to prevent an attack as they don’t know the signature of the exploit yet.
In this talk I will share my research outcomes on implementing a runtime application patching algorithm on an insecurely coded application to make it secure against code injection vulnerabilities and other logical issues related to web applications. I will introduce the next generation web application defending technology dubbed as Runtime Application Self Protection (RASP) that works by understanding your application to defend against web attacks by working inside the web application. RASP relies on Runtime Patching to inject security into web apps implicitly without introducing additional code changes. The root cause of all the code injection vulnerabilities is that the language interpreter cannot distinguish between data and code. The proposed solution will detect code context breakout to effectively detect and prevent code injections with the help of runtime hooking and patching at framework api or language api level. The research focuses mainly on detecting and preventing vulnerabilities like SQL Injection, Cross Site Scripting, Remote Command Execution, HTTP Verb Tampering, Header Injection, File Upload Bypass, Path Traversal etc and other application security challenges like Session Hijacking, Credential Stuffing and Layer 7 DDoS etc. This research is carried out by implementing a RASP module to a vulnerable web application written in python using tornado framework with sqlite backend.
API Security - OWASP top 10 for APIs + tips for pentesters



API Security - OWASP top 10 for APIs + tips for pentestersInon Shkedy The document discusses modern application security issues related to APIs. It begins with an overview of common API security risks like SQL injection, XSS, and CSRF. It then focuses on how application security has changed with the transition to modern architectures that are API-focused, use cloud infrastructure, and follow DevOps practices. Key changes discussed include less abstraction layers, clients handling more responsibility, and APIs exposing more data and endpoints directly. The document also summarizes the OWASP API security project and proposed API security top 10 risks. Real attack examples are provided to illustrate broken authorization and authentication vulnerabilities.
Checkmarx meetup API Security - API Security in depth - Inon Shkedy



Checkmarx meetup API Security - API Security in depth - Inon ShkedyAdar Weidman The document discusses modern application security challenges with APIs, provides real world examples of API vulnerabilities, and discusses solutions. It begins by introducing common API security issues like object level authorization (BOLA) and function level authorization (BFLA). It then details two real attacks - one on a food delivery app that allowed account takeover via phone number verification, and one on a social network that allowed email updating due to inconsistent authorization. The document advocates for proper authorization mechanisms and expanding the attack surface to find vulnerabilities.
Injecting Security into Web apps at Runtime Whitepaper



Injecting Security into Web apps at Runtime WhitepaperAjin Abraham This document discusses a method called Runtime Application Self Defence (RASP) to securely inject protections into web applications at runtime without requiring code changes. RASP works by hooking into critical APIs, learning an application's behavior to generate rules, and then monitoring for context breaks to prevent attacks like SQL injection and cross-site scripting. The key advantages of RASP over traditional WAFs are that it operates from within the application so it understands the application context and can prevent zero-day attacks.
OWASP Top 10 2017 rc1 - The Ten Most Critical Web Application Security Risks



OWASP Top 10 2017 rc1 - The Ten Most Critical Web Application Security RisksAndre Van Klaveren A presentation of the OWASP Top 10 2017 release candidate, expected to be finalized in summer 2017. Presented at the St. Louis CYBER meetup on Wednesday, June 7, 2017.
OWASP Top 10 - 2017 Top 10 web application security risks



OWASP Top 10 - 2017 Top 10 web application security risksKun-Da Wu The OWASP team recently released the 2017 revised version of the ten most critical web application security risks. This presentation brief the OWASP Top 10 - 2017 for you to learn more about these important security issues.
Similar to Better API Security with Automation (20)
Owasp top 10 web application security risks 2017



Owasp top 10 web application security risks 2017Sampath Bhargav Pinnam The document outlines the OWASP Top 10 application security risks for 2017. It discusses the top 10 risks which are injection, broken authentication, sensitive data exposure, XML external entities, broken access control, security misconfiguration, cross-site scripting, insecure deserialization, use of vulnerable components, and insufficient logging and monitoring. It provides details on each risk such as examples and how attackers can exploit them. The document also discusses OWASP's goal of raising awareness of application security needs and best practices for developers and organizations.
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxazida3 The document discusses validating all inputs to prevent cross-site scripting (XSS) attacks. It introduces the OWASP HTML Sanitizer Project, which is a Java library that sanitizes HTML to allow untrusted user input to be safely embedded in web pages. The sanitizer removes malicious code while keeping desired markup, through a policy-based approach. Sample usages demonstrated validate specific elements like images and links. The project aims to protect against XSS while allowing third-party content through a tested, securely-designed library.
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxjohnpragasam1 The OWASP Top Ten Proactive Controls v2 introduces new proactive controls to the Top Ten list. It includes more practical examples and contributions from the OWASP community and non-OWASP community. It also includes some best practices to consider when building mobile apps, such as secure storage, authentication, etc. The document then lists 10 proactive controls, including verifying for security early and often, parameterizing queries, encoding data, validating all inputs, implementing identity and authentication controls, implementing appropriate access controls, protecting data, implementing logging and intrusion detection, leveraging security frameworks and libraries, and handling errors and exceptions.
OWASP_Top_Ten_Proactive_Controls version 2



OWASP_Top_Ten_Proactive_Controls version 2ssuser18349f1 an introduction to OWASP top ten proactive control
OWASP_Top_Ten_Proactive_Controls_v2.pptx



OWASP_Top_Ten_Proactive_Controls_v2.pptxcgt38842 The OWASP Top Ten Proactive Controls v2 introduces new proactive controls to the Top Ten list, provides more practical examples and case studies, and has contributions from a large number of non-OWASP community members, while also including some best practices for building secure mobile applications. It outlines 10 proactive controls for application security including verifying for security early and often, parameterizing queries, encoding data before use in a parser, validating all inputs, implementing identity and authentication controls, implementing appropriate access controls, protecting data, implementing logging and intrusion detection, leveraging security frameworks and libraries, and handling errors and exceptions.
OWASP_Top_Ten_Proactive_Controls_v32.pptx



OWASP_Top_Ten_Proactive_Controls_v32.pptxnmk42194 The OWASP Top Ten Proactive Controls 2.0 document introduces new proactive controls to the Top Ten list and provides more practical examples and contributions from the community. It includes some best practices for building secure mobile apps. The document then describes 10 proactive controls addressing common vulnerabilities like injection, XSS, access control issues etc. It provides details on each control with examples and references.
apidays LIVE LONDON - Protecting financial-grade APIs - Getting the right API...



apidays LIVE LONDON - Protecting financial-grade APIs - Getting the right API...apidays apidays LIVE LONDON - The Road to Embedded Finance, Banking and Insurance with APIs
Protecting financial-grade APIs - Getting the right API Security stack!
Isabelle Mauny, CTO at 42Crunch
apidays LIVE Paris - Protecting financial grade API: adopting the right secur...



apidays LIVE Paris - Protecting financial grade API: adopting the right secur...apidays apidays LIVE Paris - Responding to the New Normal with APIs for Business, People and Society
December 8, 9 & 10, 2020
Protecting financial grade API: adopting the right security stack
Isabelle Mauny, Co-founder & Field CTO at 42Crunch
Azure App Gateway and Log Analytics under Penetration Tests



Azure App Gateway and Log Analytics under Penetration TestsRoy Kim An end to end configuration of Azure App Gateway in front of Azure App Service with Log Analytics monitoring. You will see a demo of a simple penetration test and how you can monitor and alert with Log Analytics to detect common web attacks such as SQL injection and cross site scripting with the Gateway’s Web Application Firewall. You will walk away with an understanding of how Azure App Gateway and Log Analytics is applied as a security solution.
Sergey Kochergan - OWASP Top 10 Web Application Vulnerabilities 



Sergey Kochergan - OWASP Top 10 Web Application Vulnerabilities Braindev Kyiv Sergey Kochergan is QA Engineer at Luxoft with extensive experience in software engineering and security field. As an independent consultant, he has provided strategic expertise to business clients with frameworks for SCADA security policy, organazied hackatons and ctf events. Sergey was involved into R&D projects of System Design for SDR communication hardware, network forensics with IDS.
In this lecture Sergey will tell the audience about Security in general, will make overview of nowadays Web Testing Environment and also will present his vision of Risk Rating Methodology and Vulnerability Patterns.
For our next events join us:
http://www.meetup.com/Kyiv-Dev-Meetup-SmartMonday/
https://www.facebook.com/braindevkyiv
APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...



APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security best practices like implementing zero trust architectures, considering all APIs as open, and applying fine-grained access control. The document also summarizes several real-world API vulnerabilities and breaches at companies like T-Mobile, Facebook, Uber, and Equifax to illustrate the risks. Developers are encouraged to incorporate security testing and follow secure development practices.
APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...



APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security principles like zero trust architecture and considering all APIs as open. The document gives examples of real API breaches at companies like T-Mobile, Facebook, Uber, and Equifax. It provides mitigation strategies for these issues and encourages developers to prioritize API security, implement controls like rate limiting, and test APIs for vulnerabilities.
Security in the cloud protecting your cloud apps



Security in the cloud protecting your cloud appsCenzic The document discusses security best practices for cloud applications. It notes that 75% of cyber attacks target internet applications and over 400 new vulnerabilities are discovered each month. The top vulnerabilities include cross-site scripting, SQL injection, and insecure direct object references. The document provides examples of how these vulnerabilities can be exploited by hackers and recommends best practices like input validation, output encoding, secure authentication and session management to help protect applications.
OWASP an Introduction 



OWASP an Introduction alessiomarziali This document provides an overview of the Open Web Application Security Project (OWASP). It discusses what OWASP is, the types of projects and resources it provides like publications, software tools, and local chapters. It also covers some of the software tools in more detail, like WebGoat and WebScarab, and how they can be used for application security testing and education.
The path of secure software by Katy Anton



The path of secure software by Katy AntonDevSecCon This document discusses 10 controls (C1 through C10) for developing secure software. Each control is described in 1-2 pages and addresses how it mitigates many of the top 10 risks from the OWASP list, including injection, XSS, sensitive data exposure, access control issues, and more. Specific techniques are provided, such as query parameterization to prevent SQL injection, output encoding to prevent XSS, validating all input, secure authentication and authorization practices, encrypting data, and centralized error handling.
2022 APIsecure_From Shift Left to Full Circle - A Pragmatic Approach to Catch...



2022 APIsecure_From Shift Left to Full Circle - A Pragmatic Approach to Catch...APIsecure_ Official APIsecure - April 6 & 7, 2022
APIsecure is the world’s first conference dedicated to API threat management; bringing together breakers, defenders, and solutions in API security.
From Shift Left to Full Circle - A Pragmatic Approach to Catching Up and Keeping Up With API Security
Chuck Herrin, CTO at WIB
OWASP Portland - OWASP Top 10 For JavaScript Developers



OWASP Portland - OWASP Top 10 For JavaScript DevelopersLewis Ardern With the release of the OWASP TOP 10 2017 we saw new issues rise as contenders of most common issues in the web landscape. Much of the OWASP documentation displays issues, and remediation advice/code relating to Java, C++, and C#; however not much relating to JavaScript. JavaScript has drastically changed over the last few years with the release of Angular, React, and Vue, alongside the popular use of NodeJS and its libraries/frameworks. This talk will introduce you to the OWASP Top 10 explaining JavaScript client and server-side vulnerabilities.
Outpost24 webinar - Api security



Outpost24 webinar - Api securityOutpost24 API 101 discusses how to secure web applications and APIs. APIs are used extensively in web and mobile applications to allow communication between services but this can introduce security weaknesses if not implemented properly. API attacks are a growing threat, with 90% of breaches targeting web applications and APIs projected to become the most common attack vector by 2022. The document outlines security best practices for securing APIs throughout the development lifecycle from design to testing to runtime, and how one company implemented API security testing to improve their compliance and privacy posture.
DevSecOps - automating security



DevSecOps - automating securityJohn Staveley In this presentation John will show how Azure Devops can be used to automate the deployment and security checks of a website in the Azure cloud. In this presentation we will go through how a variety of tools are used to gain security insights into your code and deployed environment. We will explore how this relates to the pull security left philosophy from DevSecOps. After the presentation you will have gained a good insight into all the tools you can use to improve the security of your deployed code base.
Web Application Security 101



Web Application Security 101Cybersecurity Education and Research Centre + Background & Basics of Web App Security, The HTTP Protocol, Web.
+ Application Insecurities, OWASP Top 10 Vulnerabilities (XSS, SQL Injection, CSRF, etc.)
+ Web App Security Tools (Scanners, Fuzzers, etc), Remediation of Web App
+ Vulnerabilities, Web Application Audits and Risk Assessment.
Web Application Security 101 was conducted by:
Vaibhav Gupta, Vishal Ashtana, Sandeep Singh from Null.
Ad
Recently uploaded (20)
COBOL Programming with VSCode - IBM Certificate



COBOL Programming with VSCode - IBM CertificateVICTOR MAESTRE RAMIREZ COBOL Programming with VSCode - IBM Certificate
Why Indonesia’s $12.63B Alt-Lending Boom Needs Loan Servicing Automation & Re...



Why Indonesia’s $12.63B Alt-Lending Boom Needs Loan Servicing Automation & Re...Prachi Desai
Alt-lenders are scaling fast, but manual loan reconciliation is cracking under pressure. See how automation solves revenue leakage and compliance chaos.
https://www.taxilla.com/loan-repayment-reconciliation
Rebuilding Cadabra Studio: AI as Our Core Foundation



Rebuilding Cadabra Studio: AI as Our Core FoundationCadabra Studio Cadabra Studio set out to reconstruct its core processes, driven entirely by AI, across all functions of its software development lifecycle. This journey resulted in remarkable efficiency improvements of 40–80% and reshaped the way teams collaborate. This presentation shares our challenges and lessons learned in becoming an AI-native firm, including overcoming internal resistance and achieving significant project delivery gains. Discover our strategic approach and transformative recommendations to integrate AI not just as a feature, but as a fundamental element of your operational structure. What changes will AI bring to your company?
Marketo & Dynamics can be Most Excellent to Each Other – The Sequel



Marketo & Dynamics can be Most Excellent to Each Other – The SequelBradBedford3 So you’ve built trust in your Marketo Engage-Dynamics integration—excellent. But now what?
This sequel picks up where our last adventure left off, offering a step-by-step guide to move from stable sync to strategic power moves. We’ll share real-world project examples that empower sales and marketing to work smarter and stay aligned.
If you’re ready to go beyond the basics and do truly most excellent stuff, this session is your guide.
From Chaos to Clarity - Designing (AI-Ready) APIs with APIOps Cycles



From Chaos to Clarity - Designing (AI-Ready) APIs with APIOps CyclesMarjukka Niinioja Teams delivering API are challenges with:
- Connecting APIs to business strategy
- Measuring API success (audit & lifecycle metrics)
- Partner/Ecosystem onboarding
- Consistent documentation, security, and publishing
🧠 The big takeaway?
Many teams can build APIs. But few connect them to value, visibility, and long-term improvement.
That’s why the APIOps Cycles method helps teams:
📍 Start where the pain is (one “metro station” at a time)
📈 Scale success across strategy, platform, and operations
🛠 Use collaborative canvases to get buy-in and visibility
Want to try it and learn more?
- Follow APIOps Cycles in LinkedIn
- Visit the www.apiopscycles.com site
- Subscribe to email list
-
Eliminate the complexities of Event-Driven Architecture with Domain-Driven De...



Eliminate the complexities of Event-Driven Architecture with Domain-Driven De...SheenBrisals The distributed nature of modern applications and their architectures brings a great level of complexity to engineering teams. Though API contracts, asynchronous communication patterns, and event-driven architecture offer assistance, not all enterprise teams fully utilize them. While adopting cloud and modern technologies, teams are often hurried to produce outcomes without spending time in upfront thinking. This leads to building tangled applications and distributed monoliths. For those organizations, it is hard to recover from such costly mistakes.
In this talk, Sheen will explain how enterprises should decompose by starting at the organizational level, applying Domain-Driven Design, and distilling to a level where teams can operate within a boundary, ownership, and autonomy. He will provide organizational, team, and design patterns and practices to make the best use of event-driven architecture by understanding the types of events, event structure, and design choices to keep the domain model pure by guarding against corruption and complexity.
Essentials of Resource Planning in a Downturn



Essentials of Resource Planning in a DownturnOnePlan Solutions In a tight labor market and tighter economy, PMOs and resource managers must ensure that every team member is focused on the highest-value work. This session explores how AI reshapes resource planning and empowers organizations to forecast capacity, prevent burnout, and balance workloads more effectively, even with shrinking teams.
Design by Contract - Building Robust Software with Contract-First Development



Design by Contract - Building Robust Software with Contract-First DevelopmentPar-Tec S.p.A. In the fast-paced world of software development, code quality and reliability are paramount. This SlideShare deck, presented at PyCon Italia 2025 by Antonio Spadaro, DevOps Engineer at Par-Tec, introduces the “Design by Contract” (DbC) philosophy and demonstrates how a Contract-First Development approach can elevate your projects.
Beginning with core DbC principles—preconditions, postconditions, and invariants—these slides define how formal “contracts” between classes and components lead to clearer, more maintainable code. You’ll explore:
The fundamental concepts of Design by Contract and why they matter.
How to write and enforce interface contracts to catch errors early.
Real-world examples showcasing how Contract-First Development improves error handling, documentation, and testability.
Practical Python demonstrations using libraries and tools that streamline DbC adoption in your workflow.
The rise of e-commerce has redefined how retailers operate—and reconciliation...



The rise of e-commerce has redefined how retailers operate—and reconciliation...Prachi Desai As payment flows grow more fragmented, the complexity of reconciliation and revenue recognition increases. The result? Mounting operational costs, silent revenue leakages, and avoidable financial risk.
Spot the inefficiencies. Automate what’s slowing you down.
https://www.taxilla.com/ecommerce-reconciliation
How AI Can Improve Media Quality Testing Across Platforms (1).pptx



How AI Can Improve Media Quality Testing Across Platforms (1).pptxkalichargn70th171 Media platforms, from video streaming to OTT and Smart TV apps, face unprecedented pressure to deliver seamless, high-quality experiences across diverse devices and networks. Ensuring top-notch Quality of Experience (QoE) is critical for user satisfaction and retention.
Bonk coin airdrop_ Everything You Need to Know.pdf



Bonk coin airdrop_ Everything You Need to Know.pdfHerond Labs The Bonk airdrop, one of the largest in Solana’s history, distributed 50% of its total supply to community members, significantly boosting its popularity and Solana’s network activity. Below is everything you need to know about the Bonk coin airdrop, including its history, eligibility, how to claim tokens, risks, and current status.
https://blog.herond.org/bonk-coin-airdrop/
Build enterprise-ready applications using skills you already have!



Build enterprise-ready applications using skills you already have!PhilMeredith3 Process Tempo is a rapid application development (RAD) environment that empowers data teams to create enterprise-ready applications using skills they already have.
With Process Tempo, data teams can craft beautiful, pixel-perfect applications the business will love.
Process Tempo combines features found in business intelligence tools, graphic design tools and workflow solutions - all in a single platform.
Process Tempo works with all major databases such as Databricks, Snowflake, Postgres and MySQL. It also works with leading graph database technologies such as Neo4j, Puppy Graph and Memgraph.
It is the perfect platform to accelerate the delivery of data-driven solutions.
For more information, you can find us at www.processtempo.com
14 Years of Developing nCine - An Open Source 2D Game Framework



14 Years of Developing nCine - An Open Source 2D Game FrameworkAngelo Theodorou A 14-year journey developing nCine, an open-source 2D game framework.
This talk covers its origins, the challenges of staying motivated over the long term, and the hurdles of open-sourcing a personal project while working in the game industry.
Along the way, it’s packed with juicy technical pills to whet the appetite of the most curious developers.
Agentic Techniques in Retrieval-Augmented Generation with Azure AI Search



Agentic Techniques in Retrieval-Augmented Generation with Azure AI SearchMaxim Salnikov Discover how Agentic Retrieval in Azure AI Search takes Retrieval-Augmented Generation (RAG) to the next level by intelligently breaking down complex queries, leveraging full conversation history, and executing parallel searches through a new LLM-powered query planner. This session introduces a cutting-edge approach that delivers significantly more accurate, relevant, and grounded answers—unlocking new capabilities for building smarter, more responsive generative AI applications.
Traditional Retrieval-Augmented Generation (RAG) pipelines work well for simple queries—but when users ask complex, multi-part questions or refer to previous conversation history, they often fall short. That’s where Agentic Retrieval comes in: a game-changing advancement in Azure AI Search that brings LLM-powered reasoning directly into the retrieval layer.
This session unveils how agentic techniques elevate your RAG-based applications by introducing intelligent query planning, subquery decomposition, parallel execution, and result merging—all orchestrated by a new Knowledge Agent. You’ll learn how this approach significantly boosts relevance, groundedness, and answer quality, especially for sophisticated enterprise use cases.
Key takeaways:
- Understand the evolution from keyword and vector search to agentic query orchestration
- See how full conversation context improves retrieval accuracy
- Explore measurable improvements in answer relevance and completeness (up to 40% gains!)
- Get hands-on guidance on integrating Agentic Retrieval with Azure AI Foundry and SDKs
- Discover how to build scalable, AI-first applications powered by this new paradigm
Whether you're building intelligent copilots, enterprise Q&A bots, or AI-driven search solutions, this session will equip you with the tools and patterns to push beyond traditional RAG.
Integration Ignited Redefining Event-Driven Architecture at Wix - EventCentric



Integration Ignited Redefining Event-Driven Architecture at Wix - EventCentricNatan Silnitsky At Wix, we revolutionized our platform by making integration events the backbone of our 4,000-microservice ecosystem. By abandoning traditional domain events for standardized Protobuf events through Kafka, we created a universal language powering our entire architecture.
We'll share how our "single-aggregate services" approach—where every CUD operation triggers semantic events—transformed scalability and extensibility, driving efficient event choreography, data lake ingestion, and search indexing.
We'll address our challenges: balancing consistency with modularity, managing event overhead, and solving consumer lag issues. Learn how event-based data prefetches dramatically improved performance while preserving the decoupling that makes our platform infinitely extensible.
Key Takeaways:
- How integration events enabled unprecedented scale and extensibility
- Practical strategies for event-based data prefetching that supercharge performance
- Solutions to common event-driven architecture challenges
- When to break conventional architectural rules for specific contexts
Software Engineering Process, Notation & Tools Introduction - Part 3



Software Engineering Process, Notation & Tools Introduction - Part 3Gaurav Sharma Software Engineering Process, Notation & Tools Introduction
Boost Student Engagement with Smart Attendance Software for Schools



Boost Student Engagement with Smart Attendance Software for SchoolsVisitu Boosting student engagement is crucial for educational success, and smart attendance software is a powerful tool in achieving that goal. Read the doc to know more.
Best Inbound Call Tracking Software for Small Businesses

Best Inbound Call Tracking Software for Small BusinessesTheTelephony The best inbound call tracking software for small businesses offers features like call recording, real-time analytics, lead attribution, and CRM integration. It helps track marketing campaign performance, improve customer service, and manage leads efficiently. Look for solutions with user-friendly dashboards, customizable reporting, and scalable pricing plans tailored for small teams. Choosing the right tool can significantly enhance communication and boost overall business growth.
How John started to like TDD (instead of hating it) (ViennaJUG, June'25)



How John started to like TDD (instead of hating it) (ViennaJUG, June'25)Nacho Cougil Let me share a story about how John (a developer like any other) started to understand (and enjoy) writing Tests before the Production code.
We've all felt an inevitable "tedium" when writing tests, haven't we? If it's boring, if it's complicated or unnecessary? Isn't it? John thought so too, and, as much as he had heard about writing tests before production code, he had never managed to put it into practice, and even when he had tried, John had become even more frustrated at not understanding how to put it into practice outside of a few examples katas 🤷♂️
Listen to this story in which I will explain how John went from not understanding Test Driven Development (TDD) to being passionate about it... so much that now he doesn't want to work any other way 😅 ! He must have found some benefits in practising it, right? He says he has more advantages than working in any other way (e.g., you'll find defects earlier, you'll have a faster feedback loop or your code will be easier to refactor), but I'd better explain it to you in the session, right?
PS: Think of John as a random person, as if he was even the speaker of this talk 😉 !
---
Presentation shared at ViennaJUG, June'25
Feedback form:
https://bit.ly/john-like-tdd-feedback
Ad
Better API Security with Automation
- 1. The API Security Platform for the Enterprise ISABELLE MAUNY - CHIEF PRODUCT OFFICER & CO-FOUNDER [email protected] BETTER SECURITY WITH AN AUTOMATED APPROACH
- 2. OWASP : FROM 2010 THROUGH 2017 2 TOP 10 2010 A1: Injection A2: Cross-Site Scripting (XSS) A3: Broken Authentication and Session Management A4: Insecure Direct Object References A5: Cross-Site Request Forgery (CSRF) A6: Security Misconfiguration A7: Insecure Cryptographic Storage A8: Failure to Restrict URL Access A9: Insufficient Transport Layer Protection A10: Unvalidated Redirects and Forwards Top 10 2017 A1: Injection* A2: Broken Authentication A3: Sensitive Data Exposure* A4: XML External Entities (XXE)* A5: Broken Access Control* A6: Security Misconfiguration* A7: Cross-Site Scripting (XSS)* A8: Insecure Deserialization* A9: Using Components with Known Vulnerabilities* A10: Insufficient Logging&Monitoring *= API related
- 3. 3By 2022 APIs will become the most common attack vector - Gartner
- 4. HOW DID WE GET THERE? 4
- 6. 6
- 8. 8
- 10. VALIDATE AND SANITIZE INPUT 10 URL validation Verb validation ✓ Reject if not valid Query params validation ✓ Min / Max / Pattern-based matching Content-Type validation ✓ Don’t accept as-is! Accept Header validation ✓ Don’t copy into Content-Type Data inbound ✓ Format ✓ Message Size and complexity Data outbound ✓ Data Leakage ✓ Exception Leakage ✓ Use rules against data dictionary 2 OPENAPI SPECIFICATION to the RESCUE !
- 11. VALIDATE JWT TOKENS 11 Don’t trust the incoming token! Validate algorithm (the one you chose!) ✓ HS256 ✓ RS256 (recommended) Reject None! Validate signature ✓ Prefer digital signatures over HMAC ✓ If not, be careful of key exchange Validate standard claims and your own claims See details Learn the best practices for keeping your JWTs secure. 3 OPENAPI SPECIFICATION (AGAIN) to the RESCUE !
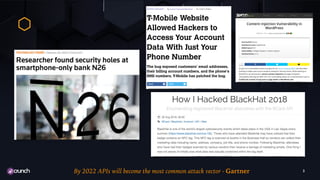
- 12. FINE-GRAIN AUTHORIZATION 12 Who is calling ? ✓ Is it your own app ? ✓ Is it a trusted user ? What can they do ? Example: T-Mobile number Scopes are often not enough ! ✓ Need ABAC solution (XACML!) 4
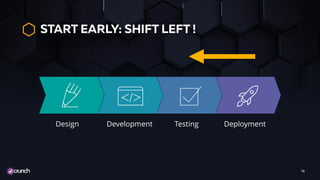
- 14. START EARLY: SHIFT LEFT ! 14 DeploymentTestingDevelopmentDesign
- 16. COVER THE BASICS 16 Automated Analysis Static code analysis 3rd party libraries validation (CVEs), e.g. NPS / Snyk for Node.js GitHub dependencies graph Manual Analysis Code reviews 1
- 17. HACK YOURSELVES! 17 API Scanning/Fuzzing ✓ Veracode, Coverity ✓ 42Crunch (coming soon!) Transport analysis ✓ SSL Labs ✓ Hardenize Further Analysis ✓ Bug Bounty ✓ Pen Testing 2
- 18. 18 PROTECT YOUR APIS 3 Protect all APIs ( public, private, SaaS) AUTOMATICALLY deploy security measures such as API Security Gateways/Firewalls ✓ Enforce Rate Limiting • Brute force attacks (see N26!) • DOS attacks ✓ Data Validation / JWT Validation / Auth / Azn ✓ Serves as Virtual Patching (as a WAF does for applications) ✓ Deploy at the edge and/or close to APIs (microservices architecture)
- 19. Use Development ticketing system for tracking issues Analyse runtime behaviour and raise issues automatically 19 MONITOR AND ANALYZE 4
- 20. JOIN THE MAILING LIST ! APISECURITY.IO NEWS AND TOOLS FOR BETTER API SECURITY
- 22. PROPOSAL FOR A DEV-SEC-OPS CYCLE FOR APIS 22 Monitor Assess Protect Test Develop Deploy Monitor Security Vulnerabilities and runtime behavior Continuous API hardening including API fuzzing Deploy to containerized PEP Configure and apply security policies from assessed risk Assess API description and evaluate risk level Develop and document API with OpenAPI/Swagger
- 23. CONTENT INJECTION: WORDPRESS API 23https://blog.sucuri.net/2017/02/content-injection-vulnerability-wordpress-rest-api.html
- 24. TITLE TEXT Remote Command Execution (A1) SQL Injection (A1) JSON injection (A1) Information Leakage (A3) Broken Access Control (A5) Check: https://blog.talosintelligence.com/2018/07/ samsung-smartthings-vulns.html 24
- 25. 25 https://www.talosintelligence.com/reports/TALOS-2018-0539/
- 26. 26 Information Leakage (A3) Broken Access Control (A5) Check: https://www1.cs.fau.de/ filepool/projects/n26/n26-roots.pdf
- 28. 28 Failed to properly validate that you can’t input any other number than yours!
- 29. UNPROTECTED API ! (A6) Remote Command Execution SQL Injection Buffer Overflow JSON injection Information Leakage Check: https://blog.talosintelligence.com/2018/07/samsung- smartthings-vulns.html 29
- 30. AND OF COURSE …. EQUIFAX FOR A9 30
- 31. JWT TOKEN VALIDATION 31 Failed to properly validate JWT token (A5) Algorithm (set to None) Claims (audience)
- 32. RESOURCES OWASP Top 10 ✓ https://www.owasp.org/index.php/Category:OWASP_Top_Ten_2017_Project OWASP DevSlop Project ✓ https://www.owasp.org/index.php/OWASP_DevSlop_Project Chaos Engineering ✓ http://principlesofchaos.org ✓ https://github.com/dastergon/awesome-chaos-engineering OWASP ZAP ✓ https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project Source Code Analysis ✓ https://www.owasp.org/index.php/Source_Code_Analysis_Tools Code Security reviews ✓ https://www.owasp.org/index.php/Code_Review_Introduction Systems Scans ✓ https://www.owasp.org/index.php/Category:Vulnerability_Scanning_Tools Security Methodology ✓ https://developer.rackspace.com/blog/fanatical-security-delivered-by-quality-engineering-security-team/ 32
- 33. RESOURCES SSL Setup Scan ✓ https://hardenize.com ✓ https://securityheaders.io ✓ https://www.ssllabs.com/ssltest/ Threat Modelling ✓ https://www.owasp.org/index.php/Application_Threat_Modeling Attacks Type Information ✓ XSS: https://excess-xss.com ✓ Buffer Overflow: https://www.youtube.com/watch?v=1S0aBV-Waeo ✓ SQL injection: https://www.youtube.com/watch?v=ciNHn38EyRc ✓ Cookie stealing /XSS: https://www.youtube.com/watch?v=T1QEs3mdJoc Pixi / DevSlop ✓ https://github.com/DevSlop/Pixi ✓ https://devslop.co JWT as session data ✓ https://dzone.com/articles/stop-using-jwts-as-session-tokens 33

