SecDevOps for API Security
0 likes255 views
As the pace at which APIs are created, proper security requires automation. This presentation introduces top OWASP issues which are occurring today and a series of steps to better protect our APIs.
1 of 34
Downloaded 28 times
































Ad
Recommended
42crunch-API-security-workshop



42crunch-API-security-workshop42Crunch If you ask about API security, you will be most likely be told about OAuth2, may be OpenID Connect and of course TLS.
But in order to properly secure APIs, you will have to address many other aspects. This presentation cover key concepts related to API Security, as well as practical tools/solutions to address the overall issue, such as:
- Transport and message encryption.
- Digital Signatures
- Auditing and non-repudiation
- SecDevOps and security as code
- Coding best practices and how to enforce them
- Infrastructure Best Practices
API Security: the full story



API Security: the full story42Crunch In this presentation, we explain why OAuth and SSL are not enough when it comes to API Security, and that you should also think about addressing other aspects such as confidentiality, integrity, audit or compliance requirements. We expose the tactics to address each of those aspects, and a set of recommendations to apply immediately to your APIs development.
Advanced API Security Patterns



Advanced API Security Patterns42Crunch While TLS and OAuth are widely used today, they are not always well-used and in many cases they are not enough. In this presentation, we introduce all aspects of security to consider as well as the OpenAPI security extensions which can be leveraged to better express the contract between the consumer and the provider.
APIDays Paris Security Workshop



APIDays Paris Security Workshop42Crunch Slides from my workshop in Paris, with practical tips on Security at the technical and organisational levels.
Why you need API Security Automation



Why you need API Security Automation42Crunch Ever faster agile development and a wide gap across development and security teams are 2 of the main reasons you want to entirely automate all aspects of API security: code scans, infra scans, security testing, automatic policies deployment and deployment of lightweight, secure enforcement points (PEPs). Let's shift left!
Presentation given at APIDays Paris in Jan 2018.
OWASP API Security Top 10 Examples



OWASP API Security Top 10 Examples42Crunch The document discusses the OWASP API Security Top 10 project which aims to raise awareness of common API vulnerabilities. It highlights some frequent issues like input validation problems, insecure configurations, and data/exception leakage. The document also demonstrates examples of these vulnerabilities using a vulnerable demo API called Pixi.
Top API Security Issues Found During POCs



Top API Security Issues Found During POCs42Crunch WATCH WEBINAR: https://youtu.be/LLVOouA4pbs
Over the past 6 months, we have discovered many similarities across APIs from companies from very different industries. "This is an eye opener" is the most recurring comment from our prospects. We thought it would be worth sharing our findings in this webinar.
Through a mix of slides and demos, we will describe the top 5 issues our security audit reports, what they are and why they matter, including:
- Potentials attacks linked to each issue
- How they can be remediated
- Example request/response and reports
Guidelines to protect your APIs from threats



Guidelines to protect your APIs from threatsIsabelle Mauny 1) The document discusses securing APIs and provides guidance on a layered approach including application level security, guiding principles like zero trust architecture, and protecting against specific API threats outlined in the OWASP API Security Top 10.
2) It summarizes real stories of API vulnerabilities from companies like Uber, Facebook, and Equifax and provides mitigations for each.
3) The key recommendations are to incorporate API security at design time, conduct security testing of APIs, and automate security through practices like DevSecOps.
API Security in a Microservices World



API Security in a Microservices World42Crunch A microservice architecture brings new challenges to API Security and careful design needs to be applied at operations and development level to ensure corporate data is properly protected from unwanted access.
In this session we explain what API security encompasses, why API security needs to be considered as early as possible in the lifecycle of the microservices, how known standards such as OAuth and OpenID Connect can be leveraged to authenticate and authorize access to microservices and give practical examples and recommendations for the design and deployment of microservice architectures.
The Dev, Sec and Ops of API Security - API World



The Dev, Sec and Ops of API Security - API World42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Applying API Security at Scale



Applying API Security at ScaleNordic APIs By Isabelle Mauny, Chief Product Officer & Co-Founder at 42Crunch
With the crazy rate at which APIs are developed, enterprises face a delicate situation to secure them. Data validation, input sanitization, security testing are tasks that require a lot of attention and time. When done very late in the API lifecycle, results are usually disastrous. API Security must be fully part of the API lifecycle, as transparent as possible, preventing developers from introducing vulnerabilities early on. A bug discovered in production can cost up to 30 times more effort to solve. Security vulnerabilities are no different.
API Security Guidelines: Beyond SSL and OAuth.



API Security Guidelines: Beyond SSL and OAuth.Isabelle Mauny This document provides guidelines for proper API security. It discusses evolving API security from established perimeters to blurry perimeters. It emphasizes that API security needs to consider authentication, authorization, integrity, confidentiality, availability, audit, and other aspects. It recommends implementing governance, evaluating coverage, establishing risk-based policies, and automating security through the full development cycle.
Protecting Microservices APIs with 42Crunch API Firewall



Protecting Microservices APIs with 42Crunch API Firewall42Crunch In loosely coupled architectures, we must put in place application level security, should it be for client traffic (North-South) or intra-microservices traffic (East-West).
In this webinar, we show you how the 42Crunch API firewall can be used to put API threat protection in place automatically, as early as design time.
We’ll use a mix of slides and demos to present:
(1) The various elements of security to consider in order to cover the full API security scope (infrastructure vs application level security)
(2) Which threat protections must be put in place in a microservices architecture, and where
(3) How to leverage OpenAPI (aka Swagger) to configure threat protection from design time
(4) How to automate threat protection deployment
OWASP API Security Top 10 - Austin DevSecOps Days



OWASP API Security Top 10 - Austin DevSecOps Days42Crunch In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Better API Security with Automation 



Better API Security with Automation 42Crunch API security needs to be thought with agility and collaboration in mind. In this presentation, we explain why API security must be automated: explosion of endpoints, continuous change, human errors and early involvement of security teams in API dev process.
OWASP API Security TOP 10 - 2019



OWASP API Security TOP 10 - 2019Miguel Angel Falcón Muñoz The document summarizes the OWASP API Security Top 10 - 2019, which outlines the top 10 most critical API security risks. It includes an introduction to the OWASP API Security Top 10 project, release notes on the first edition, a description of the risk rating methodology used, and summaries of the top 10 risks which are: 1) Broken Object Level Authorization, 2) Broken Authentication, 3) Excessive Data Exposure, 4) Lack of Resources & Rate Limiting, 5) Broken Function Level Authorization.
APISecurity_OWASP_MitigationGuide 



APISecurity_OWASP_MitigationGuide Isabelle Mauny Presentation from the OWASP 20th Anniversary conference. An overview of API Security issues and associated top 10 and how to address them.
Five Principles to API Security



Five Principles to API SecurityIsabelle Mauny This document discusses the need for API security as APIs increasingly expose enterprise data and processes both internally and externally. It notes that while APIs may seem invisible without a GUI, they can be easily discovered and are vulnerable to the same threats as web applications if not properly secured. The document advocates for a holistic approach to API security that considers authentication, authorization, integrity, confidentiality and other aspects. It also emphasizes that the right security measures depend on the type of API and calls for collaboration between operations, development, security and business teams to implement proper API security.
The Dev, Sec and Ops of API Security - NordicAPIs



The Dev, Sec and Ops of API Security - NordicAPIs42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
WEBINAR: OWASP API Security Top 10



WEBINAR: OWASP API Security Top 1042Crunch WATCH WEBINAR: https://youtu.be/zTkv_9ChVPY
In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Injecting Security into vulnerable web apps at Runtime



Injecting Security into vulnerable web apps at RuntimeAjin Abraham Web Application Security is not hard, but it’s easy to get it wrong as writing secure code is not easy as preaching. So to overcome incidents happening from such unforeseen events, organisations tend to rely on Web Application Firewalls or WAFs. Web Application Firewalls have been in the industry for a long time. Every one of them either work outside or around the web applications and act by intercepting the HTTP request coming to the web server, then take a decision to allow or block the request based on traditional signature checks. They are never aware of what is happening inside the application like how the user input is getting interpreted, Is the application/server under heavy load?, Is the attacker exfiltrating data by exploiting an SQLi that WAF couldn’t detect? etc. The strength of traditional WAF depends on manual or predefined rules/signature. As a result, they have the limitation that they will get bypassed if a payload is not present in their signature list. In the occurrence of a zero day, a WAF in most cases won’t be able to prevent an attack as they don’t know the signature of the exploit yet.
In this talk I will share my research outcomes on implementing a runtime application patching algorithm on an insecurely coded application to make it secure against code injection vulnerabilities and other logical issues related to web applications. I will introduce the next generation web application defending technology dubbed as Runtime Application Self Protection (RASP) that works by understanding your application to defend against web attacks by working inside the web application. RASP relies on Runtime Patching to inject security into web apps implicitly without introducing additional code changes. The root cause of all the code injection vulnerabilities is that the language interpreter cannot distinguish between data and code. The proposed solution will detect code context breakout to effectively detect and prevent code injections with the help of runtime hooking and patching at framework api or language api level. The research focuses mainly on detecting and preventing vulnerabilities like SQL Injection, Cross Site Scripting, Remote Command Execution, HTTP Verb Tampering, Header Injection, File Upload Bypass, Path Traversal etc and other application security challenges like Session Hijacking, Credential Stuffing and Layer 7 DDoS etc. This research is carried out by implementing a RASP module to a vulnerable web application written in python using tornado framework with sqlite backend.
REST API Security by Design with Azure Pipelines



REST API Security by Design with Azure Pipelines42Crunch WATCH WEBINAR: https://42crunch.com/webinar-questions-azure-pipelines/
REST API Static Security Testing Extension for Microsoft Azure Pipelines: https://bit.ly/42azure
Security is an important topic in software development. Unfortunately, security is usually considered too late in software development, and especially in the API lifecycle. Waiting until software and APIs are in production before addressing security concerns can be a severe risk to your organization. Did you know that vulnerabilities found in production cost up to 30x time and money more to fix?
There is a solution: by engaging developers early, educating them on API threats and uncovering real actionable issues in your APIs, you can act swiftly and save a lot of effort downstream.
In this webinar, we will
- Explain the concepts behind “shifting left” and how it can benefit your organization, both at quality and security levels.
- Explain how auditing your OpenAPI (aka Swagger) definitions gives early visibility to developers of potential security issues in APIs implementation.
- Demonstrate the functionality of the audit and which issues it detects.
- Describe how you can leverage audit at build time to ensure only contracts at the required level of security quality can be deployed.
- Demonstrate our new Azure Pipelines plugin and its discovery mechanism.
- We will be joined in the webinar by Steven Murawski from the Microsoft Azure Cloud Advocacy team.
API Security - OWASP top 10 for APIs + tips for pentesters



API Security - OWASP top 10 for APIs + tips for pentestersInon Shkedy The document discusses modern application security issues related to APIs. It begins with an overview of common API security risks like SQL injection, XSS, and CSRF. It then focuses on how application security has changed with the transition to modern architectures that are API-focused, use cloud infrastructure, and follow DevOps practices. Key changes discussed include less abstraction layers, clients handling more responsibility, and APIs exposing more data and endpoints directly. The document also summarizes the OWASP API security project and proposed API security top 10 risks. Real attack examples are provided to illustrate broken authorization and authentication vulnerabilities.
Injecting Security into Web apps at Runtime Whitepaper



Injecting Security into Web apps at Runtime WhitepaperAjin Abraham This document discusses a method called Runtime Application Self Defence (RASP) to securely inject protections into web applications at runtime without requiring code changes. RASP works by hooking into critical APIs, learning an application's behavior to generate rules, and then monitoring for context breaks to prevent attacks like SQL injection and cross-site scripting. The key advantages of RASP over traditional WAFs are that it operates from within the application so it understands the application context and can prevent zero-day attacks.
APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...



APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security best practices like implementing zero trust architectures, considering all APIs as open, and applying fine-grained access control. The document also summarizes several real-world API vulnerabilities and breaches at companies like T-Mobile, Facebook, Uber, and Equifax to illustrate the risks. Developers are encouraged to incorporate security testing and follow secure development practices.
API Security and Management Best Practices



API Security and Management Best PracticesCA API Management A look at the high-level considerations for controlling, metering and monitoring APIs from test through to production.
OISC 2019 - The OWASP Top 10 & AppSec Primer



OISC 2019 - The OWASP Top 10 & AppSec PrimerThreatReel Podcast Technology First
16th Annual Ohio Information Security Conference
OISC 2019
#OISC19
The OWASP Top 10 & AppSec Primer
By Matt Scheurer (@c3rkah)
Dayton, Ohio
Date: 03/13/2019
Abstract:
Are you testing the security of your web applications, web sites, and web servers? The malicious threat actors on the Internet almost certainly are. We will cover AppSec along with a brief review of the 2017 OWASP Top 10 List. The focus of the presentation is how to get started with AppSec and where to continue learning more. Accompanying the presentation are live demos of Nikto and the OWASP Zed Attack Proxy (ZAP).
Bio:
Matt Scheurer serves as Chair of the Cincinnati Networking Professionals Association Security Special Interest Group (CiNPA Security SIG) and works as a Systems Security Engineer in the Financial Services industry. He holds a CompTIA Security+ Certification and possesses multiple Microsoft Certifications including MCP, MCPS, MCTS, MCSA, and MCITP. He has presented on numerous Information Security topics as a featured speaker at many local area technology groups and large Information Security conferences all over the Ohio, Indiana, and Kentucky Tri-State. Matt maintains active memberships in a number of professional organizations including the Association for Computing Machinery (ACM), Cincinnati Networking Professionals Association (CiNPA), Financial Services - Information Sharing and Analysis Center (FS-ISAC), and Information Systems Security Association (ISSA).
Better API Security With A SecDevOps Approach



Better API Security With A SecDevOps ApproachNordic APIs In an ever agile world where APIs are designed and implemented at an incredible rate, securing APIs is often a last moment thought and security teams as a obstacle. Security vulnerabilities are bugs, and like any other bug must be found as early as possible. In this session, Isabelle explains how developers can take advantage of an automated approach to discover and fix security issues as early as possible and how security teams can put the right tools in place to ensure that their security requirements are met as part of the API lifecycle. We will talk about static/dynamic code analysis, OpenAPI and dynamic security policies.
APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...



APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security principles like zero trust architecture and considering all APIs as open. The document gives examples of real API breaches at companies like T-Mobile, Facebook, Uber, and Equifax. It provides mitigation strategies for these issues and encourages developers to prioritize API security, implement controls like rate limiting, and test APIs for vulnerabilities.
More Related Content
What's hot (20)
API Security in a Microservices World



API Security in a Microservices World42Crunch A microservice architecture brings new challenges to API Security and careful design needs to be applied at operations and development level to ensure corporate data is properly protected from unwanted access.
In this session we explain what API security encompasses, why API security needs to be considered as early as possible in the lifecycle of the microservices, how known standards such as OAuth and OpenID Connect can be leveraged to authenticate and authorize access to microservices and give practical examples and recommendations for the design and deployment of microservice architectures.
The Dev, Sec and Ops of API Security - API World



The Dev, Sec and Ops of API Security - API World42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Applying API Security at Scale



Applying API Security at ScaleNordic APIs By Isabelle Mauny, Chief Product Officer & Co-Founder at 42Crunch
With the crazy rate at which APIs are developed, enterprises face a delicate situation to secure them. Data validation, input sanitization, security testing are tasks that require a lot of attention and time. When done very late in the API lifecycle, results are usually disastrous. API Security must be fully part of the API lifecycle, as transparent as possible, preventing developers from introducing vulnerabilities early on. A bug discovered in production can cost up to 30 times more effort to solve. Security vulnerabilities are no different.
API Security Guidelines: Beyond SSL and OAuth.



API Security Guidelines: Beyond SSL and OAuth.Isabelle Mauny This document provides guidelines for proper API security. It discusses evolving API security from established perimeters to blurry perimeters. It emphasizes that API security needs to consider authentication, authorization, integrity, confidentiality, availability, audit, and other aspects. It recommends implementing governance, evaluating coverage, establishing risk-based policies, and automating security through the full development cycle.
Protecting Microservices APIs with 42Crunch API Firewall



Protecting Microservices APIs with 42Crunch API Firewall42Crunch In loosely coupled architectures, we must put in place application level security, should it be for client traffic (North-South) or intra-microservices traffic (East-West).
In this webinar, we show you how the 42Crunch API firewall can be used to put API threat protection in place automatically, as early as design time.
We’ll use a mix of slides and demos to present:
(1) The various elements of security to consider in order to cover the full API security scope (infrastructure vs application level security)
(2) Which threat protections must be put in place in a microservices architecture, and where
(3) How to leverage OpenAPI (aka Swagger) to configure threat protection from design time
(4) How to automate threat protection deployment
OWASP API Security Top 10 - Austin DevSecOps Days



OWASP API Security Top 10 - Austin DevSecOps Days42Crunch In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Better API Security with Automation 



Better API Security with Automation 42Crunch API security needs to be thought with agility and collaboration in mind. In this presentation, we explain why API security must be automated: explosion of endpoints, continuous change, human errors and early involvement of security teams in API dev process.
OWASP API Security TOP 10 - 2019



OWASP API Security TOP 10 - 2019Miguel Angel Falcón Muñoz The document summarizes the OWASP API Security Top 10 - 2019, which outlines the top 10 most critical API security risks. It includes an introduction to the OWASP API Security Top 10 project, release notes on the first edition, a description of the risk rating methodology used, and summaries of the top 10 risks which are: 1) Broken Object Level Authorization, 2) Broken Authentication, 3) Excessive Data Exposure, 4) Lack of Resources & Rate Limiting, 5) Broken Function Level Authorization.
APISecurity_OWASP_MitigationGuide 



APISecurity_OWASP_MitigationGuide Isabelle Mauny Presentation from the OWASP 20th Anniversary conference. An overview of API Security issues and associated top 10 and how to address them.
Five Principles to API Security



Five Principles to API SecurityIsabelle Mauny This document discusses the need for API security as APIs increasingly expose enterprise data and processes both internally and externally. It notes that while APIs may seem invisible without a GUI, they can be easily discovered and are vulnerable to the same threats as web applications if not properly secured. The document advocates for a holistic approach to API security that considers authentication, authorization, integrity, confidentiality and other aspects. It also emphasizes that the right security measures depend on the type of API and calls for collaboration between operations, development, security and business teams to implement proper API security.
The Dev, Sec and Ops of API Security - NordicAPIs



The Dev, Sec and Ops of API Security - NordicAPIs42Crunch The enterprise use of APIs is growing exponentially. Companies face a difficult choice. They must shift towards a software-based, digital approach to service and product delivery – or get left behind. Agile development, business pressure and the complexity of API security have made security teams life very complicated. And to make matters more complicated, the adoption of microservices architectures has multiplied the number of API endpoints that you have to protect.
Downside: The more APIs, the higher the security risk!
API security flaws are injected at many different levels of the API lifecycle: in requirements, development, deployment and monitoring. It is proven that detecting and fixing vulnerabilities during production or post-release time is up to 30 times more difficult than earlier in the API lifecycle. Security should be easy to considered at requirements phase, applied during development by attaching pre-defined policies to APIs and ensuring that security tests are performed as part of the continuous delivery of the APIs.
Upside: We’ll prep you with all the knowledge and tools you need to implement an automated, end-to-end API Security process that will get your dev, sec and ops teams speaking the same language.
In this presentation you will learn:
Security risks at each stage of the API lifecycle, and how to mitigate them.
How to implement an end-to-end automated API security model that development, security and operations teams will love.
How to think positive! Why a positive security model works.
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
WEBINAR: OWASP API Security Top 10



WEBINAR: OWASP API Security Top 1042Crunch WATCH WEBINAR: https://youtu.be/zTkv_9ChVPY
In recent years, large reputable companies such as Facebook, Google and Equifax have suffered major data breaches that combined exposed the personal information of hundreds of millions of people worldwide. The common vector linking these breaches – APIs. The scale and magnitude of these breaches are the reason API security has been launched into the forefront of enterprise security concerns – now forcing us to rethink the way we approach API security as a whole.
OWASP Top 10 project has for a long time been the standard list of top vulnerabilities to look for and mitigate in the world of web applications.
APIs represent a significantly different set of threats, attack vectors, and security best practices. This caused the OWASP community to launch OWASP API Security project earlier this year.
In this session we’ll discuss:
What makes API Security different from web application security
The OWASP API Security Top 10
Real world breaches and mitigation strategies for each of the risks
Injecting Security into vulnerable web apps at Runtime



Injecting Security into vulnerable web apps at RuntimeAjin Abraham Web Application Security is not hard, but it’s easy to get it wrong as writing secure code is not easy as preaching. So to overcome incidents happening from such unforeseen events, organisations tend to rely on Web Application Firewalls or WAFs. Web Application Firewalls have been in the industry for a long time. Every one of them either work outside or around the web applications and act by intercepting the HTTP request coming to the web server, then take a decision to allow or block the request based on traditional signature checks. They are never aware of what is happening inside the application like how the user input is getting interpreted, Is the application/server under heavy load?, Is the attacker exfiltrating data by exploiting an SQLi that WAF couldn’t detect? etc. The strength of traditional WAF depends on manual or predefined rules/signature. As a result, they have the limitation that they will get bypassed if a payload is not present in their signature list. In the occurrence of a zero day, a WAF in most cases won’t be able to prevent an attack as they don’t know the signature of the exploit yet.
In this talk I will share my research outcomes on implementing a runtime application patching algorithm on an insecurely coded application to make it secure against code injection vulnerabilities and other logical issues related to web applications. I will introduce the next generation web application defending technology dubbed as Runtime Application Self Protection (RASP) that works by understanding your application to defend against web attacks by working inside the web application. RASP relies on Runtime Patching to inject security into web apps implicitly without introducing additional code changes. The root cause of all the code injection vulnerabilities is that the language interpreter cannot distinguish between data and code. The proposed solution will detect code context breakout to effectively detect and prevent code injections with the help of runtime hooking and patching at framework api or language api level. The research focuses mainly on detecting and preventing vulnerabilities like SQL Injection, Cross Site Scripting, Remote Command Execution, HTTP Verb Tampering, Header Injection, File Upload Bypass, Path Traversal etc and other application security challenges like Session Hijacking, Credential Stuffing and Layer 7 DDoS etc. This research is carried out by implementing a RASP module to a vulnerable web application written in python using tornado framework with sqlite backend.
REST API Security by Design with Azure Pipelines



REST API Security by Design with Azure Pipelines42Crunch WATCH WEBINAR: https://42crunch.com/webinar-questions-azure-pipelines/
REST API Static Security Testing Extension for Microsoft Azure Pipelines: https://bit.ly/42azure
Security is an important topic in software development. Unfortunately, security is usually considered too late in software development, and especially in the API lifecycle. Waiting until software and APIs are in production before addressing security concerns can be a severe risk to your organization. Did you know that vulnerabilities found in production cost up to 30x time and money more to fix?
There is a solution: by engaging developers early, educating them on API threats and uncovering real actionable issues in your APIs, you can act swiftly and save a lot of effort downstream.
In this webinar, we will
- Explain the concepts behind “shifting left” and how it can benefit your organization, both at quality and security levels.
- Explain how auditing your OpenAPI (aka Swagger) definitions gives early visibility to developers of potential security issues in APIs implementation.
- Demonstrate the functionality of the audit and which issues it detects.
- Describe how you can leverage audit at build time to ensure only contracts at the required level of security quality can be deployed.
- Demonstrate our new Azure Pipelines plugin and its discovery mechanism.
- We will be joined in the webinar by Steven Murawski from the Microsoft Azure Cloud Advocacy team.
API Security - OWASP top 10 for APIs + tips for pentesters



API Security - OWASP top 10 for APIs + tips for pentestersInon Shkedy The document discusses modern application security issues related to APIs. It begins with an overview of common API security risks like SQL injection, XSS, and CSRF. It then focuses on how application security has changed with the transition to modern architectures that are API-focused, use cloud infrastructure, and follow DevOps practices. Key changes discussed include less abstraction layers, clients handling more responsibility, and APIs exposing more data and endpoints directly. The document also summarizes the OWASP API security project and proposed API security top 10 risks. Real attack examples are provided to illustrate broken authorization and authentication vulnerabilities.
Injecting Security into Web apps at Runtime Whitepaper



Injecting Security into Web apps at Runtime WhitepaperAjin Abraham This document discusses a method called Runtime Application Self Defence (RASP) to securely inject protections into web applications at runtime without requiring code changes. RASP works by hooking into critical APIs, learning an application's behavior to generate rules, and then monitoring for context breaks to prevent attacks like SQL injection and cross-site scripting. The key advantages of RASP over traditional WAFs are that it operates from within the application so it understands the application context and can prevent zero-day attacks.
APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...



APIdays London 2019 - API Security Tips for Developers with Isabelle Mauny, 4...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security best practices like implementing zero trust architectures, considering all APIs as open, and applying fine-grained access control. The document also summarizes several real-world API vulnerabilities and breaches at companies like T-Mobile, Facebook, Uber, and Equifax to illustrate the risks. Developers are encouraged to incorporate security testing and follow secure development practices.
API Security and Management Best Practices



API Security and Management Best PracticesCA API Management A look at the high-level considerations for controlling, metering and monitoring APIs from test through to production.
OISC 2019 - The OWASP Top 10 & AppSec Primer



OISC 2019 - The OWASP Top 10 & AppSec PrimerThreatReel Podcast Technology First
16th Annual Ohio Information Security Conference
OISC 2019
#OISC19
The OWASP Top 10 & AppSec Primer
By Matt Scheurer (@c3rkah)
Dayton, Ohio
Date: 03/13/2019
Abstract:
Are you testing the security of your web applications, web sites, and web servers? The malicious threat actors on the Internet almost certainly are. We will cover AppSec along with a brief review of the 2017 OWASP Top 10 List. The focus of the presentation is how to get started with AppSec and where to continue learning more. Accompanying the presentation are live demos of Nikto and the OWASP Zed Attack Proxy (ZAP).
Bio:
Matt Scheurer serves as Chair of the Cincinnati Networking Professionals Association Security Special Interest Group (CiNPA Security SIG) and works as a Systems Security Engineer in the Financial Services industry. He holds a CompTIA Security+ Certification and possesses multiple Microsoft Certifications including MCP, MCPS, MCTS, MCSA, and MCITP. He has presented on numerous Information Security topics as a featured speaker at many local area technology groups and large Information Security conferences all over the Ohio, Indiana, and Kentucky Tri-State. Matt maintains active memberships in a number of professional organizations including the Association for Computing Machinery (ACM), Cincinnati Networking Professionals Association (CiNPA), Financial Services - Information Sharing and Analysis Center (FS-ISAC), and Information Systems Security Association (ISSA).
Similar to SecDevOps for API Security (20)
Better API Security With A SecDevOps Approach



Better API Security With A SecDevOps ApproachNordic APIs In an ever agile world where APIs are designed and implemented at an incredible rate, securing APIs is often a last moment thought and security teams as a obstacle. Security vulnerabilities are bugs, and like any other bug must be found as early as possible. In this session, Isabelle explains how developers can take advantage of an automated approach to discover and fix security issues as early as possible and how security teams can put the right tools in place to ensure that their security requirements are met as part of the API lifecycle. We will talk about static/dynamic code analysis, OpenAPI and dynamic security policies.
APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...



APIdays Paris 2019 - API Security Tips for Developers by Isabelle Mauny, 42Cr...apidays This document provides guidance on API security for developers. It discusses common API threats like lack of input validation, insecure authentication, and authorization issues. It outlines API security principles like zero trust architecture and considering all APIs as open. The document gives examples of real API breaches at companies like T-Mobile, Facebook, Uber, and Equifax. It provides mitigation strategies for these issues and encourages developers to prioritize API security, implement controls like rate limiting, and test APIs for vulnerabilities.
apidays New York 2023 - Putting yourself out there - how to secure your publi...



apidays New York 2023 - Putting yourself out there - how to secure your publi...apidays apidays New York 2023
APIs for Embedded Business Models: Finance, Healthcare, Retail, and Media
May 16 & 17, 2023
Putting yourself out there - how to secure your public APIs
Dan Erez, Architecture Team Lead at AT&T
------
Check out our conferences at https://www.apidays.global/
Do you want to sponsor or talk at one of our conferences?
https://apidays.typeform.com/to/ILJeAaV8
Learn more on APIscene, the global media made by the community for the community:
https://www.apiscene.io
Explore the API ecosystem with the API Landscape:
https://apilandscape.apiscene.io/
APIsecure 2023 - Time to Take the "F*^!" out of ShiFt Left, Christine Bevilac...



APIsecure 2023 - Time to Take the "F*^!" out of ShiFt Left, Christine Bevilac...apidays APIsecure 2023 - The world's first and only API security conference
March 14 & 15, 2023
Time to Take the "F*^!" out of ShiFt Left
Christine Bevilacqua, API Security Evangelist at APIsec University
------
Check out our conferences at https://www.apidays.global/
Do you want to sponsor or talk at one of our conferences?
https://apidays.typeform.com/to/ILJeAaV8
Learn more on APIscene, the global media made by the community for the community:
https://www.apiscene.io
Explore the API ecosystem with the API Landscape:
https://apilandscape.apiscene.io/
apidays LIVE LONDON - Protecting financial-grade APIs - Getting the right API...



apidays LIVE LONDON - Protecting financial-grade APIs - Getting the right API...apidays apidays LIVE LONDON - The Road to Embedded Finance, Banking and Insurance with APIs
Protecting financial-grade APIs - Getting the right API Security stack!
Isabelle Mauny, CTO at 42Crunch
apidays LIVE Paris - Protecting financial grade API: adopting the right secur...



apidays LIVE Paris - Protecting financial grade API: adopting the right secur...apidays apidays LIVE Paris - Responding to the New Normal with APIs for Business, People and Society
December 8, 9 & 10, 2020
Protecting financial grade API: adopting the right security stack
Isabelle Mauny, Co-founder & Field CTO at 42Crunch
API Security Webinar : Security Guidelines for Providing and Consuming APIs



API Security Webinar : Security Guidelines for Providing and Consuming APIsDevOps Indonesia 1) The document provides guidelines for securing APIs when providing and consuming services. It outlines evaluating API risks, securing ingress API connectivity, and mapping the OWASP API security risks to the ingress API development lifecycle.
2) The guidelines include five phases for ingress API connectivity: design, development, testing, implementation, and logging/monitoring. Each OWASP API security risk is mapped to elements within these phases.
3) APIs have become critical to modern applications, but many organizations' security measures have not kept up with requirements. Robust API security policies that span the entire development lifecycle are needed to securely provide and consume services.
API Security Webinar - Security Guidelines for Providing and Consuming APIs



API Security Webinar - Security Guidelines for Providing and Consuming APIsDevOps Indonesia API Security Webinar - Security Guidelines for Providing and Consuming APIs by Faisal Yahya
Simak penjelasan dari pakar industri tentang trend dan tantangan API dalam tahun 2021. Pelajari bagaimana organisasi dapat membebaskan potensi API, untuk secara efektif menangkis serangan dan melindungi aset API. Masalah-masalah yang muncul di event API Security Challenge juga akan dibahas di sini, dan akan ada hadiah-hadiah menarik bagi semua peserta.
Agenda :
- Penelusuran trend keamanan API, tantangan dan masalah-masalah keamanan yang sering dihadapi.
- Temuan dan Statistik yang dipelajari lewat API Security Challenge
- Penelusuran solusi untuk tantangan nyata yang ditemui dalam API Security Challenges
- Pengumuman pemenang API Security Challenge
2022 APIsecure_Are your APIs Rugged Enough?



2022 APIsecure_Are your APIs Rugged Enough?APIsecure_ Official This document discusses how to design APIs to be rugged and resilient against threats. It recommends threat modeling to understand vulnerabilities and abuse cases. It also suggests implementing authorization for every endpoint, explicit anonymous access, and pinning certificates for mobile apps. Runtime protections like rate limiting, JWT validation, and security headers are also advised. Monitoring APIs in a SIEM and leveraging cloud platform protections can help detect and block attacks.
API Vulnerabilties and What to Do About Them



API Vulnerabilties and What to Do About ThemEoin Woods The document provides an agenda and introduction for a presentation on API security. The agenda includes discussing the state of API security, introducing Software Security and OWASP, reviewing the top 10 API security risks, improving software security, and providing a summary. The introduction provides background on the presenter and an overview of Endava, the company he works for. It also lists Endava's global presence and industry expertise.
API Security Best Practices and Guidelines



API Security Best Practices and GuidelinesWSO2 View on-demand: https://wso2.com/library/webinars/api-security-best-practices-and-guidelines/
Modern enterprises are increasingly adopting APIs, exceeding all predictions. With more businesses investing in microservices and the increased consumption of cloud APIs, you need to secure beyond just a handful of well-known APIs. You will need to secure a higher number of internal and external endpoints.
At the same time, security itself is a broad area and vendors implement a number of seemingly similar standards and patterns, making it very difficult for consumers to settle on the best option for securing APIs. The sheer number of options can be very confusing.
There is much to learn about API security, regardless of whether you are a novice or expert and it’s extremely important that you do because security is an integral part of any development project, including API ecosystems.
This webinar will deep-dive into the importance of API security, API security patterns, and how identity and access management (IAM) fit in the ecosystem.
DURING THE WEBINAR, WE WILL COVER:
Managed APIs
OAuth 2.0 and API security patterns
Introduction to WSO2 Identity Server
How we align with OWASP API security guidelines
The API Primer (OWASP AppSec Europe, May 2015)



The API Primer (OWASP AppSec Europe, May 2015)Greg Patton API's are everywhere now. SOA, IoT, Mobile, and Thick clients all heavily rely on web services and API's. This talk will present a primer on how to assess these services/interfaces for developers and testers alike. The introduction will include topics such as API identification, common implementations and frameworks. The bulk of the talk will focus on a assessment checklist that anyone can use to test these technologies for security flaws covering topics such as:
Authentication
Verbose-ness
Hidden Functions
Lack of Access Control
Transport Security
Tampering/Trust
Injection
OWASP API Security Top 10 - API World



OWASP API Security Top 10 - API World42Crunch This document outlines the OWASP API Security Top 10 project which identifies the top 10 risks associated with modern application programming interfaces (APIs). It describes each of the top 10 risks, including broken authentication, excessive data exposure, lack of resources and rate limiting, and insufficient logging and monitoring. For each risk, it provides real-world examples of APIs that have been exploited and mitigation strategies are proposed. Additional resources for the project are listed at the end.
Peeling the Onion: Making Sense of the Layers of API Security



Peeling the Onion: Making Sense of the Layers of API SecurityMatt Tesauro This document provides an overview of API security from multiple perspectives: API security posture, runtime security, and security testing. It discusses the complex API ecosystem involving various stakeholders. The document also outlines common API attack classes like DDoS, data breaches, and abuse of functionality. Finally, it provides key takeaways that APIs have complex interconnected systems, require coordination across teams, and need to be evaluated from different security perspectives.
apidays Australia 2023 - API Security Breach Analysis & Empowering Devs to M...



apidays Australia 2023 - API Security Breach Analysis & Empowering Devs to M...apidays apidays Australia 2023 - Platforms, Products, and People: The Power of APIs
October 11 & 12, 2023
https://www.apidays.global/australia/
API Security Breach Analysis & Empowering Devs to Make Secure APIs
Jeremy Snyder, Founder and CEO of FireTail
------
Check out our conferences at https://www.apidays.global/
Do you want to sponsor or talk at one of our conferences?
https://apidays.typeform.com/to/ILJeAaV8
Learn more on APIscene, the global media made by the community for the community:
https://www.apiscene.io
Explore the API ecosystem with the API Landscape:
https://apilandscape.apiscene.io/
Checkmarx meetup API Security - Solving security at scale - Ante Gulam



Checkmarx meetup API Security - Solving security at scale - Ante GulamAdar Weidman This document discusses API security best practices at Skyscanner. It outlines how Skyscanner uses four security squads of over 20 security engineers to implement continuous security monitoring and automation. Key practices include implementing mTLS for API traffic, role-based access control, short-lived access tokens, parameter validation, and ensuring authentication, authorization, and sensitive data protection. The document emphasizes shifting security left in the development process through design reviews, automated testing, and a real-time feedback loop to ensure long-term security improvements.
2022 apidays LIVE Helsinki & North_Future proofing API Security



2022 apidays LIVE Helsinki & North_Future proofing API Securityapidays apidays LIVE Helsinki & North: API Ecosystems - Connecting Physical and Digital
March 16 & 17, 2022
Future proofing API Security
Chuck Herrin, CTO at WIB
Apidays Helsinki 2024 - Security Vulnerabilities in your APIs by Lukáš Ďurovs...



Apidays Helsinki 2024 - Security Vulnerabilities in your APIs by Lukáš Ďurovs...apidays Security Vulnerabilities in your APIs
Lukáš Ďurovský, Staff Software Engineer at Thermo Fisher Scientific
Apidays Helsinki & North 2024 - Connecting Physical and Digital: Sustainable APIs for the Era of AI, Super and Quantum Computing (May 28 and 29, 2024)
------
Check out our conferences at https://www.apidays.global/
Do you want to sponsor or talk at one of our conferences?
https://apidays.typeform.com/to/ILJeAaV8
Learn more on APIscene, the global media made by the community for the community:
https://www.apiscene.io
Explore the API ecosystem with the API Landscape:
https://apilandscape.apiscene.io/
Black and Blue APIs: Attacker's and Defender's View of API Vulnerabilities



Black and Blue APIs: Attacker's and Defender's View of API VulnerabilitiesMatt Tesauro APIs are a foundational innovation in today’s app-driven world - and increasingly becoming the main target for attackers. How do you protect yourself? Matt Tesauro, Distinguished Engineer, will walk you through how attackers use techniques like broken object level authorization (BOLA) attacks against an API, and how attackers gain access to critical data. Understand how attackers find and exploit vulnerabilities so you can gain insight into why many traditional security approaches fail against a modern API attack. Lastly, discover what this same hack looks like on the defender’s side so you can proactively secure your APIs enabling your dev teams to go fast without breaking things.
apidays LIVE Paris 2021 - Addressing OWASP API Security Top 10 by Isabelle Ma...



apidays LIVE Paris 2021 - Addressing OWASP API Security Top 10 by Isabelle Ma...apidays API breaches are increasing, with over 350 reported publicly since October 2018. The top causes are lack of input validation, rate limiting, data/exception leakage, and authorization and authentication issues. These map to the OWASP API Security Top 10 risks. API-centric architectures expand the attack surface. To address this, security needs to be considered at design time through the API contract, which defines data constraints, authorization policies, logging, and rate limiting. Following best practices like this helps avoid vulnerabilities that are costly to fix later.
Ad
Recently uploaded (20)
Intranet Examples That Are Changing the Way We Work



Intranet Examples That Are Changing the Way We WorkBizPortals Solutions In today’s workplace, staying connected is more important than ever. Whether teams are remote, hybrid, or back in the office, communication and collaboration are at the heart of getting things done. But here’s the truth — outdated intranets just don’t cut it anymore.
Scalefusion Remote Access for Apple Devices



Scalefusion Remote Access for Apple DevicesScalefusion 🔌Tried restarting.
🔁Then updating.
🔎Then Googled a fix.
And then it crashed.
Guess who has to fix it? You. And who’ll help you? - Scalefusion.
Scalefusion steps in with real-time access, not just remote hope. Support for Apple devices that support you (and them) to do more.
For more: https://scalefusion.com/remote-access-software-mac
https://scalefusion.com/es/remote-access-software-mac
https://scalefusion.com/fr/remote-access-software-mac
https://scalefusion.com/pt-br/remote-access-software-mac
https://scalefusion.com/nl/remote-access-software-mac
https://scalefusion.com/de/remote-access-software-mac
https://scalefusion.com/ru/remote-access-software-mac
Marketing And Sales Software Services.pptx



Marketing And Sales Software Services.pptxjulia smits Marketing and Sales Software Services refer to digital solutions designed to streamline, automate, and enhance a company’s marketing campaigns and sales processes. These services include tools for customer relationship management (CRM), email marketing, lead generation, sales analytics, campaign tracking, and more—helping businesses attract, engage, and convert prospects more efficiently.
Risk Management in Software Projects: Identifying, Analyzing, and Controlling...



Risk Management in Software Projects: Identifying, Analyzing, and Controlling...gauravvmanchandaa200 a detailed Explanation of SPM aktu unit 3
How a Staff Augmentation Company IN USA Powers Flutter App Breakthroughs.pdf



How a Staff Augmentation Company IN USA Powers Flutter App Breakthroughs.pdfmary rojas With local teams and talent aligned with U.S. business hours, a staff augmentation company in the USA enables real-time communication, faster decision-making, and better project coordination. This ensures smoother workflows compared to offshore-only models, especially for companies requiring tight collaboration.
Delivering More with Less: AI Driven Resource Management with OnePlan 



Delivering More with Less: AI Driven Resource Management with OnePlan OnePlan Solutions Delivering more with less is an age-old problem. Smaller budgets, leaner teams, and greater uncertainty make the path to success unclear. Combat these issues with confidence by leveraging the best practices that help PMOs balance workloads, predict bottlenecks, and ensure resources are deployed effectively, using OnePlan’s AI forecasting capabilities, especially when organizations must deliver more with fewer people.
Custom Software Development: Types, Applications and Benefits.pdf



Custom Software Development: Types, Applications and Benefits.pdfDigital Aptech Discover the different types of custom software, their real-world applications across industries, and the key benefits they offer. Learn how tailored solutions improve efficiency, scalability, and business performance in this comprehensive overview.
Top 10 Mobile Banking Apps in the USA.pdf



Top 10 Mobile Banking Apps in the USA.pdfLL Technolab 📱💸 Top Mobile Banking Apps in the USA!
Are you thinking to invest in mobile banking apps in USA? If yes, then explore this infographic and know the top 10 digital banking apps which creating ripples in USA. From seamless money transfers to powerful budgeting tools, these apps are redefining how America banks on the go.
Micro-Metrics Every Performance Engineer Should Validate Before Sign-Off



Micro-Metrics Every Performance Engineer Should Validate Before Sign-OffTier1 app When it comes to performance testing, most engineers instinctively gravitate toward the big-picture indicators—response time, memory usage, throughput. But what about the smaller, more subtle indicators that quietly shape your application’s performance and stability? we explored the hidden layer of performance diagnostics that too often gets overlooked: micro-metrics. These small but mighty data points can reveal early signs of trouble long before they manifest as outages or degradation in production.
From garbage collection behavior and object creation rates to thread state transitions and blocked thread patterns, we unpacked the critical micro-metrics every performance engineer should assess before giving the green light to any release.
This session went beyond the basics, offering hands-on demonstrations and JVM-level diagnostics that help identify performance blind spots traditional tests tend to miss. We showed how early detection of these subtle anomalies can drastically reduce post-deployment issues and production firefighting.
Whether you're a performance testing veteran or new to JVM tuning, this session helped shift your validation strategies left—empowering you to detect and resolve risks earlier in the lifecycle.
The rise of e-commerce has redefined how retailers operate—and reconciliation...



The rise of e-commerce has redefined how retailers operate—and reconciliation...Prachi Desai As payment flows grow more fragmented, the complexity of reconciliation and revenue recognition increases. The result? Mounting operational costs, silent revenue leakages, and avoidable financial risk.
Spot the inefficiencies. Automate what’s slowing you down.
https://www.taxilla.com/ecommerce-reconciliation
Shortcomings of EHS Software – And How to Overcome Them



Shortcomings of EHS Software – And How to Overcome ThemTECH EHS Solution Shortcomings of EHS Software—and What Overcomes Them
What you'll learn in just 8 slides:
- 🔍 Why most EHS software implementations struggle initially
- 🚧 3 common pitfalls: adoption, workflow disruption, and delayed ROI
- 🛠️ Practical solutions that deliver long-term value
- 🔐 Key features: centralization, security, affordability
- 📈 Why the pros outweigh the cons
Perfect for HSE heads, plant managers, and compliance leads!
#EHS #TECHEHS #WorkplaceSafety #EHSCompliance #EHSManagement #ehssoftware #safetysoftware
Online Queue Management System for Public Service Offices [Focused on Municip...



Online Queue Management System for Public Service Offices [Focused on Municip...Rishab Acharya This report documents the design and development of an Online Queue Management System tailored specifically for municipal offices in Nepal. Municipal offices, as critical providers of essential public services, face challenges including overcrowded queues, long waiting times, and inefficient service delivery, causing inconvenience to citizens and pressure on municipal staff. The proposed digital platform allows citizens to book queue tokens online for various physical services, facilitating efficient queue management and real-time wait time updates. Beyond queue management, the system includes modules to oversee non-physical developmental programs, such as educational and social welfare initiatives, enabling better participation and progress monitoring. Furthermore, it incorporates a module for monitoring infrastructure development projects, promoting transparency and allowing citizens to report issues and track progress. The system development follows established software engineering methodologies, including requirement analysis, UML-based system design, and iterative testing. Emphasis has been placed on user-friendliness, security, and scalability to meet the diverse needs of municipal offices across Nepal. Implementation of this integrated digital platform will enhance service efficiency, increase transparency, and improve citizen satisfaction, thereby supporting the modernization and digital transformation of public service delivery in Nepal.
zOS CommServer support for the Network Express feature on z17



zOS CommServer support for the Network Express feature on z17zOSCommserver The IBM z17 has undergone a transformation with an entirely new System I/O hardware and architecture model for both storage and networking. The z17 offers I/O capability that is integrated directly within the Z processor complex. The new system design moves I/O operations closer to the system processor and memory. This new design approach transforms I/O operations allowing Z workloads to grow and scale to meet the growing needs of current and future IBM Hybrid Cloud Enterprise workloads. This presentation will focus on the networking I/O transformation by introducing you to the new IBM z17 Network Express feature.
The Network Express feature introduces new system architecture called Enhanced QDIO (EQDIO). EQDIO allows the updated z/OS Communications Server software to interact with the Network Express hardware using new optimized I/O operations. The new design and optimizations are required to meet the demand of the continuously growing I/O rates. Network Express and EQDIO build the foundation for the introduction of advanced Ethernet and networking capabilities for the future of IBM Z Hybrid Cloud Enterprise users.
The Network Express feature also combines the functionality of both the OSA-Express and RoCE Express features into a single feature or adapter. A single Network Express port supports both IP protocols and RDMA protocols. This allows each Network Express port to function as both a standard NIC for Ethernet and as an RDMA capable NIC (RNIC) for RoCE protocols. Converging both protocols to a single adapter reduces Z customers’ cost for physical networking resources. With this change, IBM Z customers can now exploit Shared Memory Communications (SMC) leveraging RDMA (SMC-R) technology without incurring additional hardware costs.
In this session, the speakers will focus on how z/OS Communications Server has been updated to support the Network Express feature. An introduction to the new Enhanced QDIO Ethernet (EQENET) interface statement used to configure the new OSA is provided. EQDIO provides a variety of simplifications, such as no longer requiring VTAM user defined TRLEs, uses smarter defaults and removes outdated parameters. The speakers will also cover migration considerations for Network Express. In addition, the operational aspects of managing and monitoring the new OSA and RoCE interfaces will be covered. The speakers will also take you through the enhancements made to optimize both inbound and outbound network traffic. Come join us, step aboard and learn how z/OS Communications Server is bringing you the future in network communications with the IBM z17 Network Express feature.
Feeling Lost in the Blue? Exploring a New Path: AI Mental Health Counselling ...



Feeling Lost in the Blue? Exploring a New Path: AI Mental Health Counselling ...officeiqai AI mental health counselling sounds high-tech, but it's designed to be simple and comforting. Click here to explore how it works and why it helps!
Secure and Simplify IT Management with ManageEngine Endpoint Central.pdf



Secure and Simplify IT Management with ManageEngine Endpoint Central.pdfNorthwind Technologies ManageEngine Endpoint Central (formerly known as Desktop Central) is an all-in-one endpoint management solution designed for managing a diverse and distributed IT environment. It supports Windows, macOS, Linux, iOS, Android, and Chrome OS devices, offering a centralized approach to managing endpoints — whether they’re on-premise, remote, or hybrid.
AI Alternative - Discover the best AI tools and their alternatives



AI Alternative - Discover the best AI tools and their alternativesAI Alternative AIAlternative.co is a comprehensive directory designed to help users discover, compare, and evaluate AI tools across various domains. Its primary goal is to assist individuals and businesses in finding the most suitable AI solutions tailored to their specific needs.
Key Features
- Curated AI Tool Listings: The platform offers detailed information on a wide range of AI tools, including their functionalities, use cases, and alternatives. This allows users to make informed decisions based on their requirements.
- Alternative Suggestions: For each listed AI tool, aialternative.co provides suggestions for similar or alternative tools, facilitating easier comparison and selection.
- Regular Updates: The directory is consistently updated to include the latest AI innovations, ensuring users have access to the most current tools available in the market.
Browse All Tools here: https://aialternative.co/
List Unfolding - 'unfold' as the Computational Dual of 'fold', and how 'unfol...



List Unfolding - 'unfold' as the Computational Dual of 'fold', and how 'unfol...Philip Schwarz In this deck we look at the following:
* how unfolding lists is the computational dual of folding lists
* different variants of the function for unfolding lists
* how they relate to the iterate function
Risk Management in Software Projects: Identifying, Analyzing, and Controlling...



Risk Management in Software Projects: Identifying, Analyzing, and Controlling...gauravvmanchandaa200
Ad
SecDevOps for API Security
- 1. The API Security Platform for the Enterprise ISABELLE MAUNY - CTO & CO-FOUNDER [email protected] SEC-DEV-OPS AN AUTOMATED APPROACH TO API SECURITY
- 2. OWASP : FROM 2010 THROUGH 2017 2 For 2013, the OWASP Top 10 Most Critical Web Application Security Risks are: • A1 Injection • A2 Broken Authentication and Session Management • A3 Cross-Site Scripting (XSS) • A4 Insecure Direct Object References • A5 Security Misconfiguration • A6 Sensitive Data Exposure • A7 Missing Function Level Access Control • A8 Cross-Site Request Forgery (CSRF) • A9 Using Components with Known Vulnerabilities • A10 Unvalidated Redirects and Forwards • For 2010, the OWASP Top 10 Most Critical Web Application Security Risks are: • A1: Injection • A2: Cross-Site Scripting (XSS) • A3: Broken Authentication and Session Management • A4: Insecure Direct Object References • A5: Cross-Site Request Forgery (CSRF) • A6: Security Misconfiguration • A7: Insecure Cryptographic Storage • A8: Failure to Restrict URL Access • A9: Insufficient Transport Layer Protection • A10: Unvalidated Redirects and Forwards • • Top 10 2017 • A1:2017-Injection • A2:2017-Broken Authentication • A3:2017-Sensitive Data Exposure • A4:2017-XML External Entities (XXE) • A5:2017-Broken Access Control • A6:2017-Security Misconfiguration • A7:2017-Cross-Site Scripting (XSS) • A8:2017-Insecure Deserialization • A9:2017-Using Components with Known Vulnerabilities • A10:2017-Insufficient Logging&Monitoring
- 4. CONTENT INJECTION: WORDPRESS API 4https://blog.sucuri.net/2017/02/content-injection-vulnerability-wordpress-rest-api.html
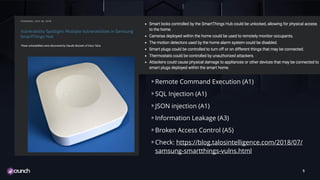
- 5. TITLE TEXT Remote Command Execution (A1) SQL Injection (A1) JSON injection (A1) Information Leakage (A3) Broken Access Control (A5) Check: https://blog.talosintelligence.com/2018/07/ samsung-smartthings-vulns.html 5
- 6. 6 https://www.talosintelligence.com/reports/TALOS-2018-0539/
- 7. 7 Information Leakage (A3) Broken Access Control (A5) Check: https://www1.cs.fau.de/ filepool/projects/n26/n26-roots.pdf
- 9. 9 Failed to properly validate that you can’t input any other number than yours!
- 10. UNPROTECTED API ! (A6) Remote Command Execution SQL Injection Buffer Overflow JSON injection Information Leakage Check: https://blog.talosintelligence.com/2018/07/samsung- smartthings-vulns.html 10
- 11. AND OF COURSE …. EQUIFAX FOR A9 11
- 12. JWT TOKEN VALIDATION 12 Failed to properly validate JWT token (A5) Algorithm (set to None) Claims (audience)
- 13. HOW DID WE GET THERE? 13
- 15. 15
- 17. 17
- 19. VALIDATE AND SANITIZE INPUT 19 URL validation Verb validation ✓ Reject if not valid ✓ Reject if user not-authorized Query params validation ✓ Min / Max / Pattern-based matching Content-Type validation ✓ Don’t accept as-is! Accept Header validation ✓ Don’t copy into Content-Type Data inbound ✓ Format ✓ Message Size and complexity Data outbound ✓ Data Leakage ✓ Exception Leakage ✓ Use rules against data dictionary 2 OPEN API to the RESCUE !
- 20. VALIDATE JWT TOKENS 20 Don’t trust the incoming token! Validate algorithm (the one you chose!) ✓ HS256 ? ✓ RS256 (recommended) Reject None Validate signature ✓ Prefer digital signatures over HMAC ✓ If not, be careful of key exchange Validate standard claims Add your own claims 3 OPEN API to the RESCUE !
- 21. EXTERNAL TOKEN VS. INTERNAL JWT 21 Token Server Validate/ Issue token
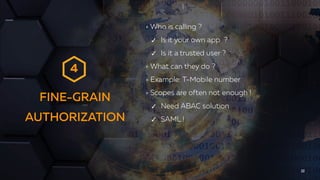
- 22. FINE-GRAIN AUTHORIZATION 22 Who is calling ? ✓ Is it your own app ? ✓ Is it a trusted user ? What can they do ? Example: T-Mobile number Scopes are often not enough ! ✓ Need ABAC solution ✓ SAML ! 4
- 24. START EARLY: SHIFT LEFT ! 24 DeploymentTestingDevelopmentDesign
- 25. COVER THE BASICS 25 Automated Analysis Static code analysis 3rd party libraries validation (CVEs) NPS / Snyk for Node.js GitHub dependencies graph Manual Analysis Code reviews 1
- 26. HACK YOURSELVES! 26 API Scanning/Fuzzing ✓ Veracode, Coverity ✓ 42Crunch (alpha) Further Analysis ✓ Bug Bounty ✓ Pen Testing 2
- 27. PROTECTION 27
- 28. 28 PROTECT YOUR APIS 1 Deploy security measures such as API Security Gateways/Firewalls ✓ Introduce Rate Limiting • Brute force attacks (see N26!) • DOS attacks ✓ Security Policies automatically applied and enforced ✓ Serves as Virtual Patching for protection ✓ Deploy at the edge and/or close to APIs (microservices architecture)
- 29. Use Development ticketing system for tracking issues Analyse runtime behaviour and raise issues automatically 29 MONITOR AND ANALYZE 2
- 30. 42CRUNCH DEV-SEC-OPS CYCLE FOR APIS 30 Monitor Assess Protect Test Develop Deploy Monitor Security Vulnerabilities and runtime behavior Continuous API hardening including API fuzzing Deploy to containerized PEP Configure and apply security policies from assessed risk Assess API description and evaluate risk level Develop and document API with OpenAPI/Swagger
- 31. TITLE TEXTHOW SECURITY PEOPLE FEEL ABOUT APIS 31
- 32. CONTACT: [email protected] WWW.42CRUNCH.COM The API Security Platform for the Enterprise
- 33. RESOURCES OWASP Top 10 ✓ https://www.owasp.org/index.php/Category:OWASP_Top_Ten_2017_Project OWASP DevSlop Project ✓ https://www.owasp.org/index.php/OWASP_DevSlop_Project Chaos Engineering ✓ http://principlesofchaos.org ✓ https://github.com/dastergon/awesome-chaos-engineering OWASP ZAP ✓ https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project Source Code Analysis ✓ https://www.owasp.org/index.php/Source_Code_Analysis_Tools Code Security reviews ✓ https://www.owasp.org/index.php/Code_Review_Introduction Systems Scans ✓ https://www.owasp.org/index.php/Category:Vulnerability_Scanning_Tools 33
- 34. RESOURCES SSL Setup Scan ✓ https://hardenize.com ✓ https://securityheaders.io ✓ https://www.ssllabs.com/ssltest/ Threat Modelling ✓ https://www.owasp.org/index.php/Application_Threat_Modeling Attacks Type Information ✓ XSS: https://excess-xss.com ✓ Buffer Overflow: https://www.youtube.com/watch?v=1S0aBV-Waeo ✓ SQL injection: https://www.youtube.com/watch?v=ciNHn38EyRc ✓ Cookie stealing /XSS: https://www.youtube.com/watch?v=T1QEs3mdJoc Pixi / DevSlop ✓ https://github.com/DevSlop/Pixi ✓ https://devslop.co JWT as session data ✓ https://dzone.com/articles/stop-using-jwts-as-session-tokens 34



