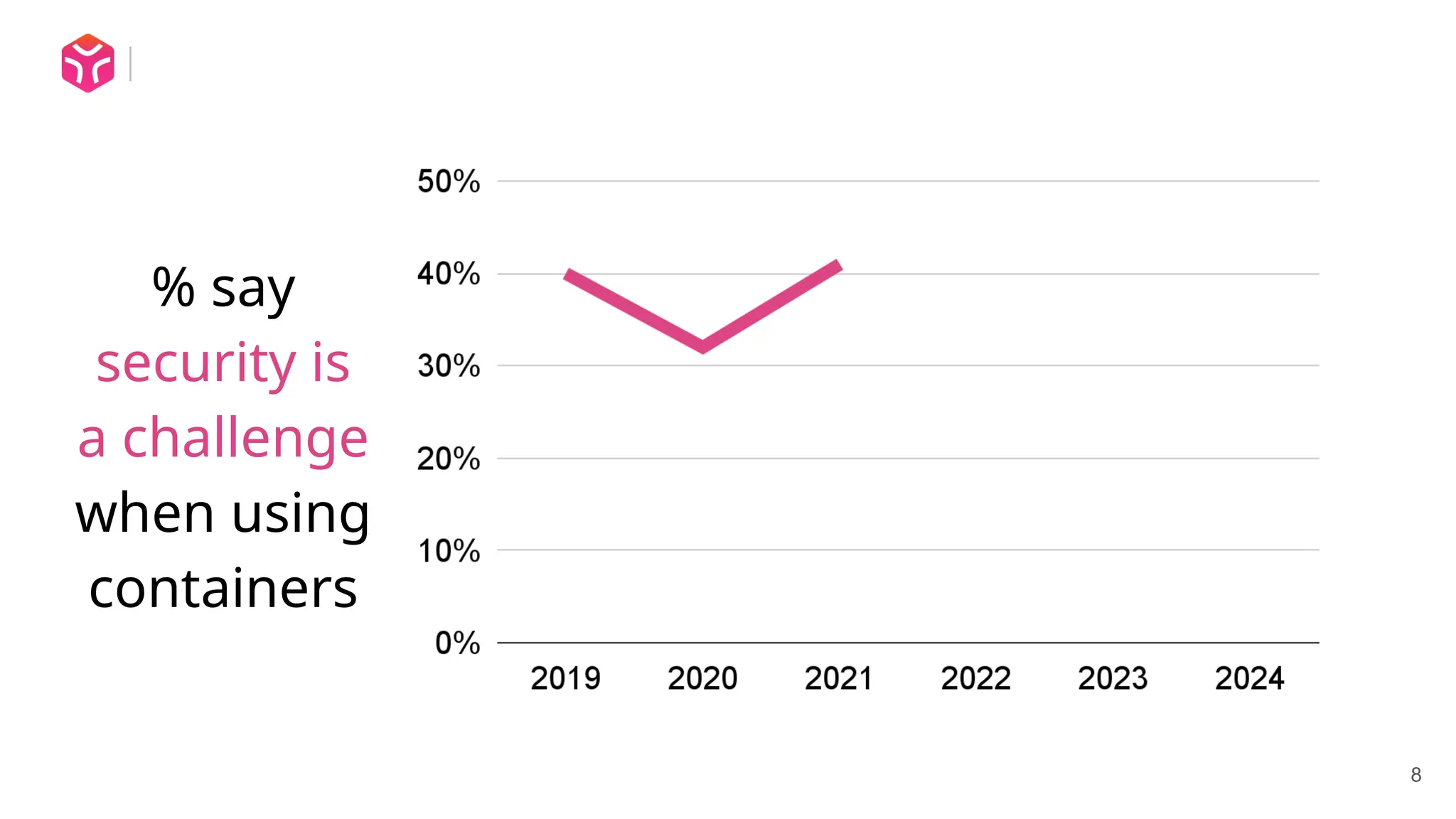
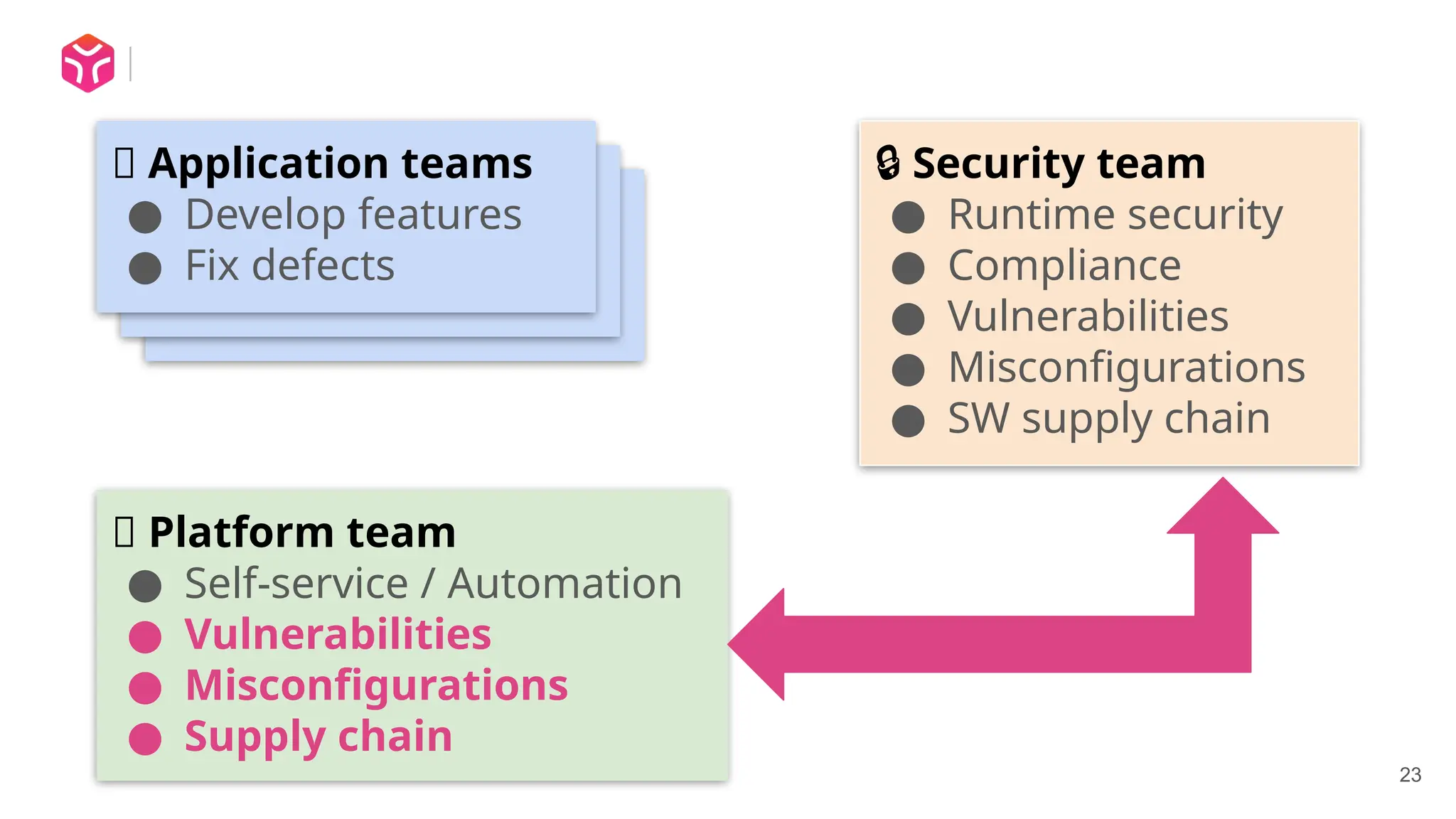
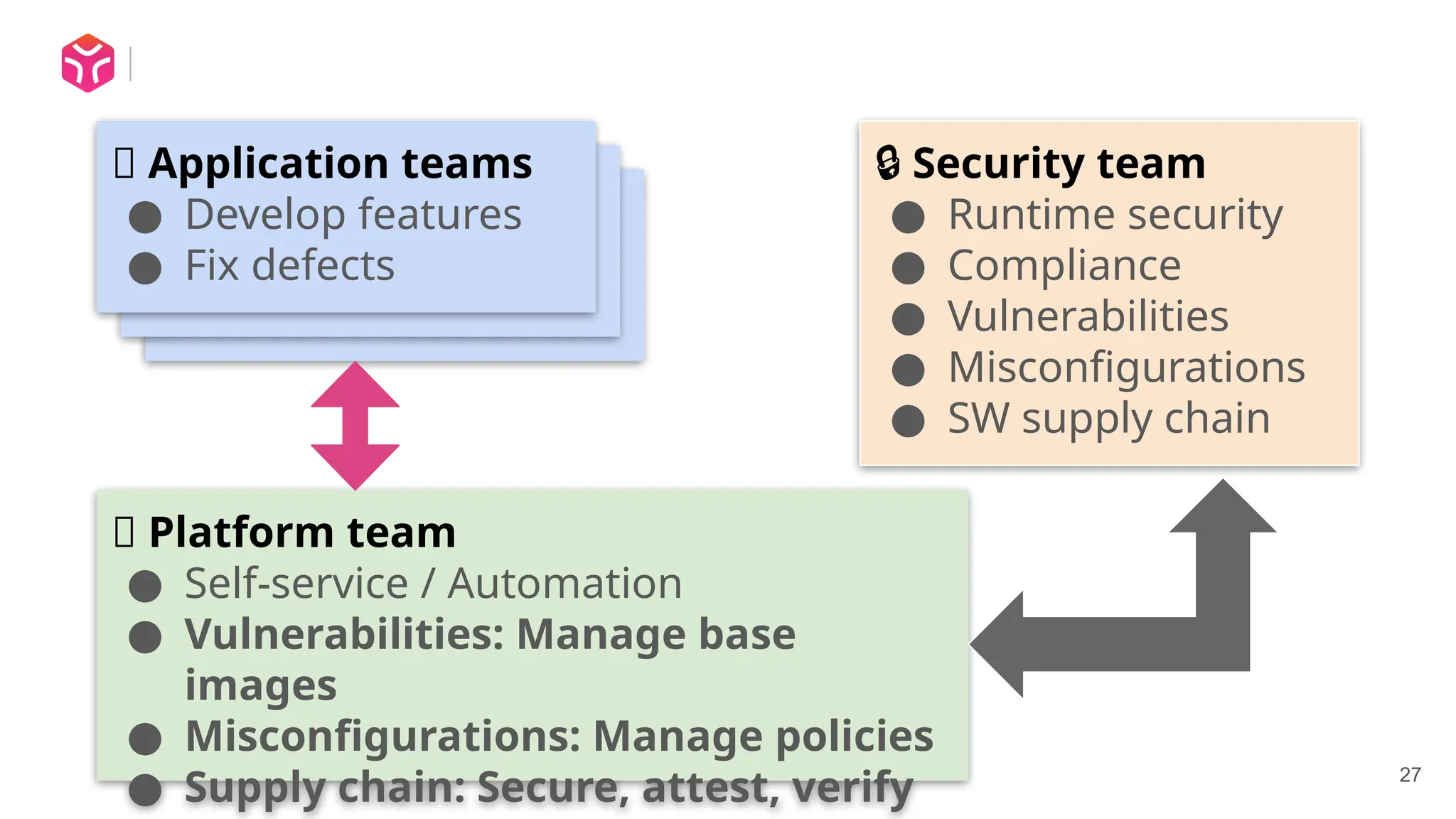
In this talk I discuss some of the fundamental challenges of security in a Kubernetes, cloud native environment, and how Shift-Down Security can help.
Reading: https://github.com/kubernetes/sig-security/blob/main/sig-security-docs/papers/shift-down/shift-down-security.md#shift-down-security