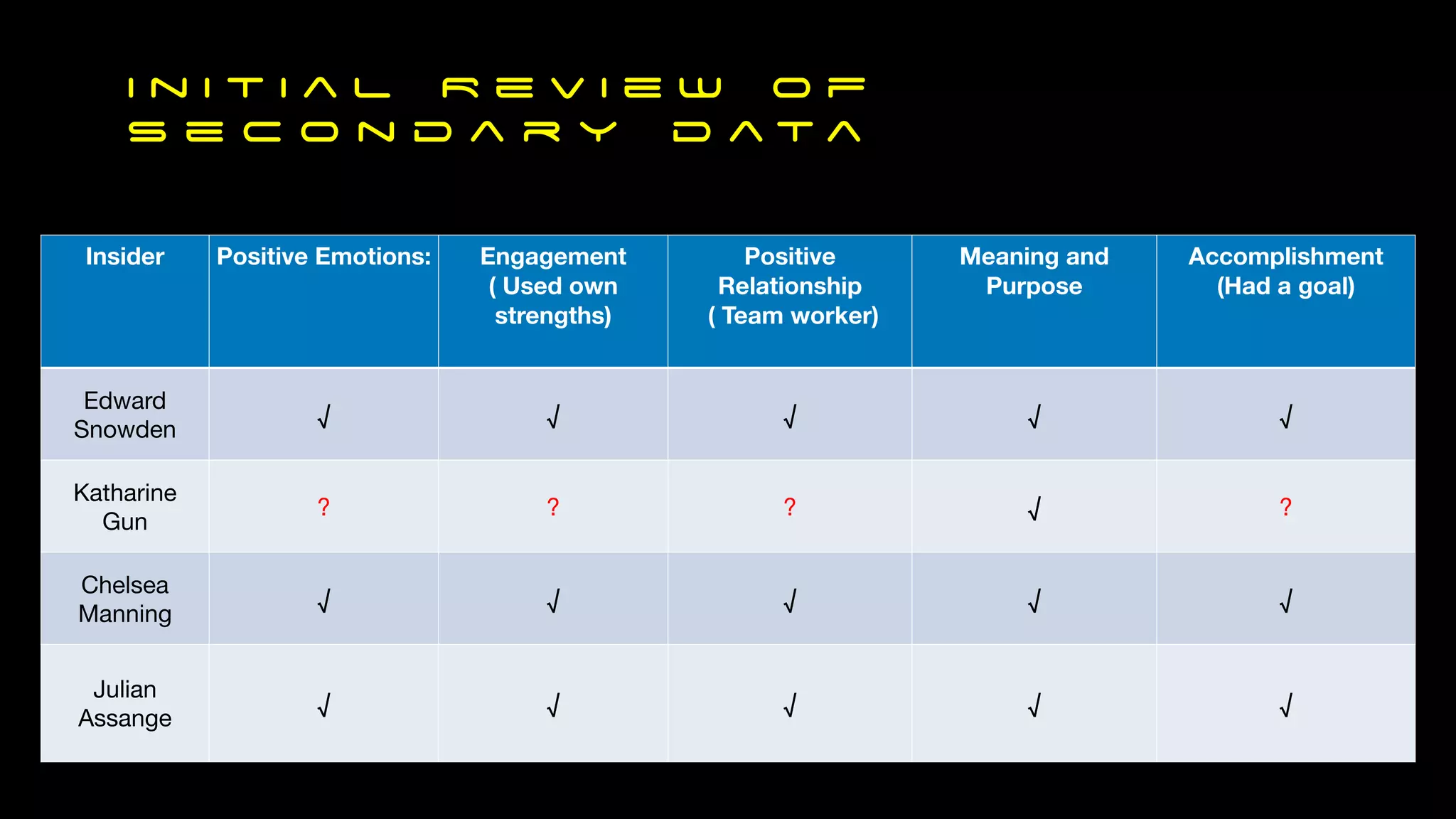
The document discusses the complexities of cyber attacks, which often stem from both external and internal sources, emphasizing the significance of identifying precursor indicators to prevent such attacks. It highlights various hypotheses about failure indicators in both natural and unnatural systems, suggesting that cyber attacks can display patterns similar to other failures. Additionally, it calls for improved behavioral analysis and intervention strategies to mitigate insider threats and enhance overall cybersecurity resilience.