InnoDB Tablespace Encryption
- 1. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | InnoDB Tablespace Encryption By Satya Bodapati Copyright © 2014, Oracle and/or its affiliates. All rights reserved. |
- 2. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 2 Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, code, or functionality, and should not be relied upon in making purchasing decisions. The development, release, and timing of any features or functionality described for Oracle’s products remains at the sole discretion of Oracle.
- 3. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 3 Program Agenda ❏Introduction ❏How to use it ❏Architecture ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 4. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 4 Program Agenda ❏Introduction ❏How to use it ❏Architecture ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 5. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 5 Introduction InnoDB supports data encryption for all file_per_table tablespaces InnoDB uses two tier encryption architecture [More on this later] There are two types of keyring plugins available for Key Management ➢keyring_file plugin - Available in all MySQL Editions ➢keyring_okv plugin - Available only in MySQL Enterprise Edition
- 6. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 6 Program Agenda ❏Introduction ❏How to use it ❏Architecture ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 7. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 7 Prerequisites ●MySQL 5.7 ●keyring plugin installed and active (only one) ●innodb_file_per_table=ON (default : ON)
- 8. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 8 Use early-plugin-load in my.cnf Why early-plugin-load? Because keyring plugin should be loaded before InnoDB is loaded. InnoDB will need the keyring plugin to decrypt tablespaces before applying redo log
- 9. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 9 Verify that Keyring plugin is loaded The status of the keyring plugin should be ACTIVE OR
- 10. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 10 All Set! Lets create first encrypted table
- 11. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 11 Where is the location of keyring_file data It is very important file. Remember to backup this file. Losing this keyring data file will make tables inaccessible.
- 12. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 12 How to encrypt existing tables? ● ALTER TABLE mydb.mytab ENCRYPTION=“Y” ALGORITHM=COPY; ● ALTER TABLE mydb.mytab ENCRYPTION=“N” ALGORITHM=COPY; ● ALGORITHM=INPLACE is not supported when turning encryption ON/OFF
- 13. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 13 Program Agenda ❏Introduction ❏How to use it ❏Architecture ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 14. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 14 Architecture MySQL keyring plugin provides a way for MySQL components to retain or cache security data, authentication keys, encryption keys, passwords, passphrases in the MySQL Server kernel. The MySQL Keyring makes its data available to internal mysql components and plugins.
- 15. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 15 Architecture InnoDB tablespace encryption uses a two tier encryption key architecture, consisting of a master encryption key and tablespace keys. Master Key The key that is used to encrypt and decrypt the tablespace key Tablespace key (aka private key) The key that is used to encrypt and decrypt tablespace data Secret keys are never ever seen by users – only internalcode
- 16. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. |Confidential – Oracle Highly Restricted Architecture Diagram: 2 Tier Architecture 16 DISK Unencrypted files MySQL Server Plugin & Services Infrastruct ure InnoDB Client keyring_okv plugin • Master Key • Stored outside the database • Oracle Key Vault : KMIP 1.2 Compliant Key Vault • Tablespace Key • Stored in tablespace header • Protected by master key Master Key Encrypted 2 Encrypted 1 keyring_file plugin Master Key Plain file ORKey Vault
- 17. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 17 Architecture keyring_file plugin stores the Master Key in a file at a location decided by keyring_file_data For encrypted tables, Tablespace key is encrypted by Master Key and stored in Tablespace header page. Encryption algorithm used is AES only. Encryption mode used is block encryption mode (CBC mode).
- 18. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 18 Architecture
- 19. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 19 Architecture
- 20. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 20 Architecture In InnoDB, pages are encrypted using the tablespace key. This is done at IO layer. Benefits are: • A page could be modified multiple times in buffer pool and then gets flushed. So we avoid encrypting the data page everytime it changed. We only encrypt just before writing page to disk • The encryption is done by background page cleaner threads. This means the query threads don’t spend extra CPU [Set appropriate number of page cleaner threads]
- 21. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 21 Architecture • The buffer pool pages remain decrypted and so there is no overhead for pages accessed. The pages are decrypted only when they are read. Limitations: • General Tablespaces (Shared Tablespaces) are not encrypted, system tablespace (ibdata*) is not encrypted. • Undo Log, redo Logs and binary logs are not encrypted • Advanced Encryption Standard (AES) is the only supported encryption algorithm.
- 22. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 22 Architecture • You cannot move or copy an encrypted table from a file- per-table tablespace to an unsupported InnoDB tablespace type • Migration from the keyring_file plugin to the keyring_okv plugin, or vice-versa • Altering the ENCRYPTION attribute of a table is an ALGORITHM=COPY operation. ALGORITHM=INPLACE is not supported
- 23. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Performance Impact • Sysbench tests did not indicate any significant impact on performance when compared to unencrypted tables • Tablespace keys are cached for faster access • Key rotation : Fast because only tablespace keys are reencrypted Confidential – Oracle Highly Restricted 23
- 24. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 24 Program Agenda ❏Introduction ❏How to use it ❏Design ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 25. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 25 Key rotation • The master encryption key should be rotated periodically • Rotating the master encryption key only changes the master encryption key and re-encrypts tablespace keys. It does not decrypt or re-encrypt associated tablespace data. • SQL to do rotation: ALTER INSTANCE ROTATE INNODB MASTER KEY;
- 26. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 26
- 27. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 27 Program Agenda ❏Introduction ❏How to use it ❏Design ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 28. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Exporting Encrypted Tablespace • Source – USE mydb; FLUSH TABLES mytab FOR EXPORT; • For encrypted table, <tablespace_name>.cfp file is generated – Copy .ibd/.cfg/.cfp file to destination – USE mydb; UNLOCK TABLES; • Destination – ALTER TABLE mydb.mytab DISCARD TABLESPACE; – Copy imported files to database directory – ALTER TABLE mydb.mytab IMPORT TABLESPACE; • .cfp file contains temporary key used to encrypt tablespace key. Should be handled carefully. Confidential – Oracle Highly Restricted 28
- 29. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 29 Program Agenda ❏Introduction ❏How to use it ❏Design ❏Key rotation ❏Import/Export ❏Replication ❏MySQL Enterprise Transparent Data Encryption
- 30. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Replication • Master and slave should use different keyring file • Tables do not use same key at master and slave – At each node, encryption uses different set of keys • Key rotation : Generates different set of master key at each node – Slaves must have keyring plugin available if master performs key rotation – If master creates encrypted tables, slave should be configured with encryption Confidential – Oracle Highly Restricted 30
- 31. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | 31 Program Agenda ❏Introduction ❏How to use it ❏Design ❏Key rotation ❏MySQL Enterprise Transparent Data Encryption
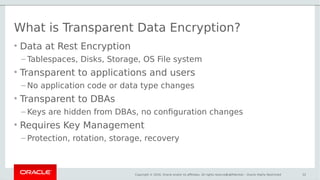
- 32. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | What is Transparent Data Encryption? • Data at Rest Encryption – Tablespaces, Disks, Storage, OS File system • Transparent to applications and users – No application code or data type changes • Transparent to DBAs – Keys are hidden from DBAs, no configuration changes • Requires Key Management – Protection, rotation, storage, recovery Confidential – Oracle Highly Restricted 32
- 33. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Transparent Data Encryption in MySQL • Data at Rest Encryption – Tablespace Encryption • Key Protection – Achieved through Oracle Key Vault • Strong Encryption – AES 256 • Simple to Manage – One master key for whole MySQL instance – One key per tablespace • High Performance & Low Overhead – Simple Key Rotation without massive decrypt/encryption costs Confidential – Oracle Highly Restricted 33
- 34. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Why Key Vault? Confidential – Oracle Highly Restricted 34
- 35. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Benefits of using Key Vault • Protected and Exclusive storage for key materials – Ensures that keys are safely stored away from database • Centralized repo for managing keys for multiple servers – One stop solution to deploy TDE on multiple database servers – Keys are accessible only to corresponding endpoint (or group of endpoints) • Secure communication – Protected through TLSv1.2 • Automatic provisioning – DBA intervention is not needed as long as endpoint is configured correctly Confidential – Oracle Highly Restricted 35
- 36. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Benefits of using Key Vault ● Key lifecycle management – Critical for standard for Payment Card Industry (PCI), Data Security Standard (DSS) – Possible to define policies for key rotation and remind user about the same – Report generation to validate compliance ● Maintains key history – Useful in restore scenarios ● Key utilization tracking – Useful in identifying suspicious usage of keys Confidential – Oracle Highly Restricted 36
- 37. Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Copyright © 2016, Oracle and/or its affiliates. All rights reserved. | Thank You! Q&A ? Copyright © 2014, Oracle and/or its affiliates. All rights reserved. |





![Copyright © 2016, Oracle and/or its affiliates. All rights
reserved. |
5
Introduction
InnoDB supports data encryption for all file_per_table
tablespaces
InnoDB uses two tier encryption architecture [More on this
later]
There are two types of keyring plugins available for Key
Management
➢keyring_file plugin - Available in all MySQL Editions
➢keyring_okv plugin - Available only in MySQL Enterprise
Edition](https://image.slidesharecdn.com/innodbtablespaceencryption-161220104313/85/InnoDB-Tablespace-Encryption-5-320.jpg)














![Copyright © 2016, Oracle and/or its affiliates. All rights
reserved. |
20
Architecture
In InnoDB, pages are encrypted using the tablespace key.
This is done at IO layer. Benefits are:
• A page could be modified multiple times in buffer pool and
then gets flushed. So we avoid encrypting the data page
everytime it changed. We only encrypt just before writing
page to disk
• The encryption is done by background page cleaner
threads. This means the query threads don’t spend extra
CPU [Set appropriate number of page cleaner threads]](https://image.slidesharecdn.com/innodbtablespaceencryption-161220104313/85/InnoDB-Tablespace-Encryption-20-320.jpg)