Introduction to backwards learning algorithm
- 1. 1 Introduction to Backward Learning Algorithm for creating Bridges by Roshan Karunarathna
- 2. 2 Contents • Before we learn Algorithm • Data Link Layer • Interconnection Devices • LAN • Limits of LAN • Interconnecting LANs • Bridge • What is bridge • Backward learning Algorithm
- 3. 3 Data Link Layer • In the seven-layer OSI model of computer networking, the data link layer is layer 2. In TCP/IP reference model, it corresponds to, or is part of the link layer. • The data link layer is the protocol layer that transfers data between adjacent network nodes in a wide area network or between nodes on the same local area network segment.
- 4. 4 Interconnection Devices Interconnection devices are used to inter connect networks at the different layers of the network architecture. The devices can operate at: – the physical layer such as optical repeaters, hubs, digital cross connects, etc. – the data link layer such as LAN switches/bridges, frame relay switches, etc., – the network layer such as a router or a gateway – the transport layer for TCP segment switching – the application layer for overlay networks such as content delivery networks
- 5. 5 Interconnection Devices Ethernet Ethernet Ethernet Repeater Autonomous System Autonomous SystemBridge Gateway Router
- 6. 6 Limits of a LAN • One shared LAN can limit us in terms of: – Distance – Number of nodes – Performance • How do we scale to a larger, faster network? – We must be able to interconnect LANs
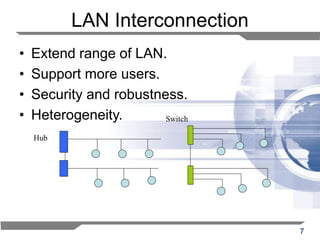
- 7. 7 LAN Interconnection • Extend range of LAN. • Support more users. • Security and robustness. • Heterogeneity. Hub Switch
- 8. 8 Interconnecting Different LANs • Conversion between different frame formats. – E.g., different frame lengths. • Speed mismatch. – Buffering. • Security. – Different security services provided by different DLLs/MACs.
- 9. 9 LAN Interconnection: Example • Multiple LANs connected by a backbone.
- 10. 10 Bridges • Connect LANs. • Operate at the DLL. – Route based on DLL addresses. • Distinction between bridges, switches, and routers gets fuzzier as technology advances.
- 11. 11 Repeaters and Bridges • Repeaters: – Extend scope of LANs. – Serve as amplifiers. – No storage/routing capabilities. • Bridges: – Also extend scope of LANs. – Routing/storage capabilities.
- 12. 12 Bridges and Extended LANs • “Transparently” interconnect LANs – Receive frames from each LAN and forward to the other – Each LAN is its own domain; a bridge is not a repeater – Could have many ports or join to a remote LAN bridge
- 13. 13
- 14. 14 More on Bridges • Have multiple interfaces, 1 per LAN. • Use destination address to forward unicast frames; if destination is on the same LAN, drops frame; otherwise forwards it. • Forward all broadcast frames. • Have storage and routing capability.
- 15. 15 More on Bridges • No additional encapsulation. • But they may have to do header conversion if interconnecting different LANs (e.g., 802.3 to 802.4 frame). • May interconnect more than 2 LANs. • LANs may be interconnected by more than 1 bridge.
- 16. 16 Bridges from 802.x to 802.y • Operation of a LAN bridge from 802.11 to 802.3.
- 17. 17 Routing • Routing is the process of forwarding of a packet in a network so that it reaches its intended destination. The main goals of routing are: • Correctness • Simplicity • Robustness • Stability • Fairness • Optimality
- 18. 18 Routing with Bridges • Bridge decides to relay frame based on destination MAC address. • If only 2 LANs, decision is simple. • If more complex topologies, routing is needed, i.e., frame may traverse more than 1 bridge.
- 19. 19 Routing with Bridges B 1 4 5 8 Frames for 5->8. Frames for 1->4 LAN A LAN B
- 20. 20 Routing with Bridges (Cont’d) • Listens to all frames on LAN A and accepts those addressed to stations on LAN B. • Retransmits frames onto B. • Does the same for B-to-A traffic.
- 21. 21 Transparent Bridges • Plug them in and they work! • How do they work? – Promiscuous mode operation. – Upon receiving frame, decide whether to forward it or not. – Routing table mapping destination addresses to outgoing interface.
- 22. 22 • The concept of backwards learning is very simple: • Learn about an (source) address from the direction from which it came, then place that address in a table and use it for (destination) forwarding. • Bridges operate in promiscuous mode, they listen to all traffic that is broadcast on every link connected to its active ports. • By examining the source MAC address of every packet traversing the link associated with a particular port on the bridge, the bridge learns what addresses are reachable via that particular port. • These addresses are stored in a forwarding database or table Backward Learning Algorithm
- 23. 23 Every LAN switch/Bridge maintains a forwarding database or table. This table contains the following fields: • MAC address • Outgoing Port number • Timer – indicating age of entry The table can be interpreted as follows: A machine with MAC address lies in direction of outgoing port number. The entry is timer time units old. Backward Learning Algorithm
- 24. 24 Backward Learning Algorithm • To increase overall performance: – Shouldn’t forward AB or CD, should forward AC and DB • How does the bridge know? – Learn who is where by observing source addresses – Forward using destination address; age for robustness
- 25. 25 Backward Learning Algorithm • used by transparent bridges. • When a bridge starts, its routing table is empty. – So, it floods: every incoming frame is forwarded in all outgoing interfaces, except the one the frame was received. – In promiscuous mode, bridge sees all frames. – They look at the frame’s source and “remember” which LAN it came from. – Entries are time stamped and expire after a certain interval. • Allows for topology changes.
- 26. 26 Backward Learning (Cont’d) • If source LAN = destination LAN, discard frame. • If source LAN <>destination LAN, forward frame. – If destination LAN unknown, flood frame.
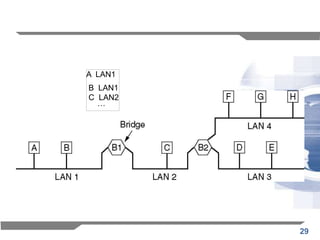
- 28. 28 • As the bridges are connected in a loop free tree topology, • the flooding will terminate at the leaves of the tree. • we illustrate the operation of the backwards learning algorithm by stepping through an example of a frame transmission • through a single LAN switch with an initially empty forwarding table.
- 29. 29 A LAN1 B LAN1 C LAN2 …
- 30. 30
- 31. 31
- 32. 32
- 33. 33
- 34. 34
- 35. 35 Bridge 1 Bridge 2 MAC Address Port MAC Address Port A 1 A 1 C 2 C 1 E 2 E 2
- 36. 36 In this method the routing tables at each node gets modified by information from the incoming packets. One way to implement backward learning is to include the identity of the source node in each packet, together with a hop counter that is incremented on each hop. When a node receives a packet in a particular line, it notes down the number of hops it has taken to reach it from the source node. If the previous value of hop count stored in the node is better than the current one then nothing is done but if the current value is better then the value is updated for future use. The problem with this is that when the best route goes down then it cannot recall the second best route to a particular node. Hence all the nodes have to forget the stored informations periodically and start all over again. Further more….
- 37. 37 Thank You! Q & A now……
Editor's Notes
- #11: Routers route based on layer 3 addresses Three cases: Some times people may have there own LAN and they may wanted to be connected There may be geographically spreaded so need cable ex Ethernet only 200m When we need to breake a LAN into parts
- #14: LAN switches are multi port (more than 4 port) bridges. LAN switches are touted by manufacturers as high throughput multi interface devices that can interconnect ports at a variety of speeds, e.g., 10M, 100M, 1G and 10Gpbs. They are also able to operate the links in full duplex mode if directly connected to a network device1. To increase their speed of operation, LAN switches, like hubs, use cut through switching. Once the destination address has been processed the packet is forwarded to the appropriate output port where transmission can be commenced if the link is idle.
- #18: Correctness: The routing should be done properly and correctly so that the packets may reach their proper destination. Simplicity: The routing should be done in a simple manner so that the overhead is as low as possible. With increasing complexity of the routing algorithms the overhead also increases. Robustness: Once a major network becomes operative, it may be expected to run continuously for years without any failures. The algorithms designed for routing should be robust enough to handle hardware and software failures and should be able to cope with changes in the topology and traffic without requiring all jobs in all hosts to be aborted and the network rebooted every time some router goes down. Stability: The routing algorithms should be stable under all possible circumstances. Fairness: Every node connected to the network should get a fair chance of transmitting their packets. This is generally done on a first come first serve basis. Optimality: The routing algorithms should be optimal in terms of throughput and minimizing mean packet delays. Here there is a trade-off and one has to choose depending on his suitability.
- #24: The MAC address refers to the destination address in the MAC frame. The outgoing port number refers to the port that needs to be used to transmit the frame for that particular MAC address. The timer is used to control the age of the entries. When a timer expires, the entry is deleted from the table. Every MAC address hit refreshes the timer of that MAC address entry.
- #29: If a bridge sees a frame with a destination address that matches one of the entries in its forwarding table, it will copy the packet into its buffer and forward the packet to the necessary port. If the outgoing port is the same as the incoming port, it discards the frame. If the bridge sees a frame for which it has no entry in its forwarding table, it will make multiple copies of the frame and broadcast it on every outgoing port (excluding the port
- #35: If we now take an example of two bridges and observe the process by which a the forwarding table is filled, we will understand the backwards learning algorithm and how it is used by the bridges in promiscuous mode. we show a sample network with two bridges. Host A initially sends a frame to host F. This is followed by a frame from host C to host A and then a third frame from host E to host C. Bridge 1 will receive the frame on port 1. With its forwarding table empty, Bridge 1 will flood the frame on outging port 2. Bridge 2 receives the frame on port 1, it too does not find an entry in its table and proceeds to flood the frame on outgoing port 2. Destination F finally receives the frame. During this flooding process, both Bridges 1 and 2 learnt that MAC address A is associated with port 1 on their respective bridges. The second frame from host C to host A will cause no flooding as both bridges have an entry for MAC address A. Bridge 2 will ignore the frame as its association for MAC address A is with port 1 on which it received the frame. But before discarding the frame it will make an entry in its forwarding table for MAC address C. Bridge 1 will receive the frame on port 2 and forward the frame to port 1 based upon the entry for MAC address A in its forwarding table. It too will make a new entry in the forwarding table for MAC address C. The third frame from host E to host C will not cause flooding either as both bridges have now an entry for MAC address C. Bridge 2 will forward the frame from port 2 to port 1 and at the same time enter MAC address E in the forwarding table. Bridge 1 will ignore the frame as the outgoing port is the same as the received port. It too will make a new entry in the forwarding table for MAC address E. Below we show the resulting forwarding tables (ignoring the timer field).
- #36: Why can’t we build a large network using bridges? Little control over forwarding paths Size of bridge forwarding tables grows with number of hosts Broadcast traffic flows freely over whole extended LAN Spanning tree algorithm limits reconfiguration speed Poor solution for connecting LANs with different MAC protocols
- #37: The bridges must reside in a loop free topology because they use flooding to find a destination. In Figure 7 below we show an example of a typical meshed bridged network. Meshed networks are popular for they can tolerate a certain number of link and device failures without creating a disconnected segment.