Introduction to the Fundamentals of Computer Networks
- 1. Computer Networks course code(502482-3) Dr. Amr Rashed
- 2. EDUCATION January 2021 Ph.D In Electronics & Communications Engineering Faculty of Engineering, Mansoura university, Mansoura January 2010 M.Sc In Electronics & Communications Engineering Faculty of Engineering, Mansoura university, Mansoura January 2005 B.Sc. In Electronics & Communications Engineering Faculty of Engineering, Mansoura university, Mansoura DR . AMR EZ Z EL- DIN R ASHED LECTURER DEPARTMENT OF COMPUTER ENGINEERING COLLEGE OF CIT RESEARCH INTERESTS AI, Deep learning, FPGA, VHDL, MATLAB, DSP, DIP, Encryption, Computer Vision, Embedded Systems, Electronics CONTACTS 0554404723 [email protected] Taif, KSA EXPERIENCE Assistant lecture at FE, Mansoura university Assistant lecture at MET institute Trainer at Jelecomm, New Horizon, ITshare, Egycet
- 3. References 1- Behrouz Forouzan; Data Communications and Networking – 5th edition, the McGraw-Hill Companies. 2- Andrew Tanenbaum and David Wetherall; Computer Networks, 5th Edition,2011 ,Prentice Hall, Pearson. 3- Andrew Tanenbaum, Feamster and David Wetherall ,Computer Networks, Global Edition 6th Edition, 2021,Prentice Hall, Pearson. 4- James F. Kurose , Keith W. Ross , Computer Networking: A Top-Down Approach (6th Edition) 6th Edition Essential References Materials
- 4. Course contents • Chapter 1: Introduction. • Chapter 2: Network Models (OSI Model ,TCP/IP model). • Chapter 3:Data & Signals - Forouzan • Chapter 4:Data link layer • Chapter 5:Network devices (Network infrastructure: cables , hub, router, switch,..) • Chapter 6:Network layer (protocols) • Chapter 7: Transport layer (TCP/UDP)---ref ->top-down approach, Kurose-Ross • Chapter 8: Application layer(HTTP,FTP,SMTP)
- 5. Chapter 1 contents 1. USES OF COMPUTER NETWORKS 2. TYPES OF COMPUTER NETWORKS 3. NETWORK TECHNOLOGY, FROM LOCAL TO GLOBAL 4. EXAMPLES OF NETWORKS 5. NETWORK PROTOCOLS 6. REFERENCE MODELS 7. STANDARDIZATION 8. POLICY, LEGAL, AND SOCIAL ISSUES 9. METRIC UNITS
- 6. Introduction • Past three centuries was dominated by a single new technology. • 18th century: great mechanical systems accompanying()المصاحبة Industrial Revolution. • 19th century: steam engine. • 20th century: Information gathering, processing, and distribution. • Other noted developments: telephone networks, invention of radio and television, extraordinary growth of computer, launching of communication satellites and the Internet.
- 7. USES OF COMPUTER NETWORKS • Computing industry has made spectacular ()مذهل progress. • The coming together of computers and communications has profound()عميق effect on the organization of computer systems. Old model of a single computer serving all of the organization's computational needs replaced by number of separate but interconnected computers. • These systems are called computer networks. • "computer network" to mean a collection of interconnected, autonomous()مستقل computing devices. • Two computers are interconnected if they can exchange information. Interconnection can be using transmission media copper wire, fiber optic cable, and radio waves (e.g., microwave, infrared, communication satellites) etc.
- 8. USES OF COMPUTER NETWORKS 1. Access ()الوصولto Information 2. Person-to-Person Communication 3. Electronic Commerce 4. Entertainment 5. The Internet of Things
- 9. 1. Access to Information A common way of accessing information via the Internet is using a Web browser, from Web sites, social media sites. Mobile applications on smartphones can access remote information . News establishments ) ( مؤسسات have largely migrated ) ( ترحيل online . Access to information, e.g., news online, reach far larger and broader audiences. Online publishing and content on social media platforms supports a funding model that depends on highly targeted behavioral advertising . Online digital libraries, professional organizations, such as the ACM and IEEE Computer Society, have all their journals and conference proceedings online . Most information on Internet is accessed using a client-server model, where a client explicitly requests information from a server
- 10. Access to Information Client-server model is widely used and forms the basis of many network usage . Most popular realization is Web application, where a server generates Web pages on its database in response to client requests . Client-server model is applicable when client and server far apart . For example, person at home accesses a page on the World wide Web, or remote Web server and user's personal computer, the client . One server may handle a large number (thousands) of clients simultaneously . In client-server model, two processes, one on the client and other on the server machine. Communication, client process sending a message over the network to the server process. Client process waits for a reply message. When server process gets request, it performs the requested work and sends back a reply .
- 11. Access to Information Another model for accessing information is peer-to-peer communication . Individuals forming a loose group can communicate with others in the group, as shown . Every person can communicate with one or more people; no fixed division into clients and servers . Many peer-to-peer systems, such as BitTorrent. do not have a central database of content . Each user maintains a local database of content . A new user can access to existing member to see what he has . This lookup process can be repeated indefinitely to build up a large local database . Peer-to-peer communication often used to share music and videos . Around 2000, a music sharing service called Napster, was shut down after a monumental copyright infringement case ( .)والنشر الطبع لحقوق ضخمة انتهاك قضية In peer-to-peer system there are no fixed clients and servers.
- 12. 2. Person-to-Person Communication Person-to-person communication is telephone of 19th century . Email used daily by millions of people, contains audio, video as well as text and pictures. Many Internet users now rely on instant messaging to communicate . Derived from the UNIX talk program around 1970, allows two people to type messages at each other in real time . Multi-person messaging services, e.g., Twitter service, lets people send short messages (including video) called "tweets" to followers around the Globe . The Internet applications includes audio (e.g., Internet radio stations, streaming music services), video (e.g., Netflix, YouTube), and - distance learning, hugely important to geographically challenged people . Between person-to-person communications and accessing information are social network applications . Facebook Let's people create and update personal profiles and shares the updates with people who are their friends . wiki, a collaborative Web site that members of a community edit Most famous wiki is the Wikipedia, an encyclopedia anyone can read or edit. WIKIPEDIA --+ The Free Encyclopedia
- 13. 3. E-Commerce • Online shopping is already popular; users can browse the online products of thousands of companies and have shipped right to their doorsteps. • Many people pay their bills, manage bank accounts, and handle their investments electronically. • Financial technology Or “fintect” applications allow users to transfer money between bank accounts, or even between friends. • online auctions or second-hand goods have become a massive industry. • Unlike traditional e-commerce, which was client-server model, online auctions are peer-to-peer where consumers can act as both buyers and sellers, although central server holds the database of products for sale. • Some forms of e-commerce have acquired cute little tags based on the fact that ''to" and "2" are pronounced the same.
- 15. 4. Entertainment • Users can find, buy, and download MP3 songs and high-definition movie. • TV shows reach many homes via IPTV (IP Television) systems based on IP technology instead of cable TV or radio transmissions. • Media streaming applications where users tune to Internet radio stations or watch recent episodes ()حلقات of their favorite TV shows or movies. • These content can be moved around your house between different devices, displays, and speakers, usually via a wireless network. • New films may become interactive, where user is prompted for story direction (القصة توجيه للمستخدم يمكن ((should Macbeth murder the king or just bide his time?) with alternative scenarios provided for all cases. • Live television become interactive, with the audience participating in quiz shows, choosing among contestants()المتنافسين . Multi-person real-time simulation games, like hide-and-seek()الغميضة in a virtual dungeon()سجن, and flight simulators. • Virtual worlds provide a persistent setting(المستمر )االعداد in which thousands of users experience a shared reality with 3D graphics.
- 16. 5. The Internet of Things (IOT) • Ubiquitous (االنتشار )واسع computing, in which computing is embedded into everyday life. • Many homes are already wired with security systems that include door and window sensors. • There are many more sensors that can be folded into a smart home monitor, such as energy consumption. • Smart electricity, gas and water meters could also report usage over the network. • This functionality saves the company money as there is then no need to send people to read the meters. • As the cost of sensing and communication drops, more and more measurement and reporting will be done with networks
- 17. The Internet of Things (IOT) Some high-end cameras already have a wireless network capability and use it to send photos to a nearby display for viewing Professional sports photographers can also send their photos to their editors in real-time . Devices such as televisions that plug into the wall can use power-line networks to send information throughout the house over the wires that carry electricity . Objects that we do not think of as computers may sense and communicate information too (shower may record water usage) .
- 18. TYPES OF COMPUTER NETWORKS 1. Broadband Access Networks 2. Mobile and Wireless Access Networks 3. Content Provider Networks (CPN) 4. Transit(عابر )مرور Networks 5. Enterprise()مؤسسة Networks
- 19. TYPES OF COMPUTER NETWORKS • There are many distinct types of computer networks: • To access Internet (mobile and broadband access networks); • Those that house the data and applications (data-center networks); • Those that connect access networks to data centers (transit networks); • Those in campus(الجامعي )الحرم , office building, or other organization (enterprise networks).
- 20. 1.Broadband Access Networks • People initially bought computers for word processing and games. Now People buy home computer for Internet access. • Internet access provides home users with connectivity to remote computers. • They can access information, communicate with other people, and buy products and services. • Bob Metcalfe. inventor of Ethernet" hypothesized that the value of a network is proportional to square of the number of users because this is roughly the numbs of different connections that may be made". • This hypothesis known as "Metcalfe’s law.”, it explains the tremendous popularity of the Internet comes from its size. • Broadband access networks are multiplying and delivered to homes through copper (e.g., telephone lines), coaxial cable (e.g., cable), or optical fiber.
- 21. 2.Mobile and Wireless Access Networks • Mobile computers, such as laptops, tablets, and smartphones, are fastest-growing segments of the computer industry. • People use their mobile devices to read and send email, tweet, watch movies, download music, play games, look at map, or simply to surf the Web for information or fun. • Lot of interest in wireless networks as wired connection is impossible in cars, boats, and airplanes. • Cellular networks operated by telephone companies are one familiar kind of wireless network that blankets us with coverage for mobile phones • Wireless hotspots based on the 802.11 standard are another kind of wireless network for mobile computers and portable devices such as phones and tablets • Wireless networks are of great value to fleets()اساطيل of trucks, taxis, delivery vehicles, and repair-persons for keeping in contact with their home base • For example, ride sharing companies such as UBER and Lyft service. • Wireless networking and mobile are not identical.
- 22. Mobile and Wireless Access Networks Wireless networks are also important to the military . If you have to be able to fight a war anywhere on Earth at short notice, counting on using the local networking infrastructure is probably not a good idea. It is better to bring your own . Conversely, some wireless computers are not mobile . In people’s homes, and in offices or hotels that lack suitable cabling, it can be more convenient to connect desktop computers or media players wirelessly than to install wires . Installing a wireless network may require simply buying a small box with some electronics in it, unpacking it, and plugging it in . Combinations of wireless networks and mobile computing.
- 23. Mobile and Wireless Access Networks • Example :air- ports, car rental return clerks work in the parking lot with wireless mobile computers. • They scan the barcodes or RFID chips of returning cars, and their mobile device, which has a built-in printer, calls the main computer, gets the rental information, and prints out the bill on the spot. • Smartphones combine aspects of mobile phones and mobile computers. • These phones connect to wireless hotspots, too, and automatically switch between networks to choose the best option for the user. • Text messaging or texting (or SMS -Short Message Service) over the cellular network was tremendously popular at its outset. • Typing short text messages on mobile phones was, for a time, an immense ()هائل money maker for mobile carriers. • Now, many alternatives that use either the phone’s cellular data plan or wireless network, including WhatsApp, Signal, and Facebook Messenger, have overtaken SMS.
- 24. Mobile and Wireless Access Networks- GPS • Mobile phones typically know their own locations. • GPS (Global Positioning System) can directly locate a device, and mobile phones often also triangulate between Wi-Fi hotspots with known locations to determine their location. • Mobile maps, directions and searches for a nearby bookstore or Chinese restaurant, or a local weather forecast. • Other services may record location, such as annotating()تأشير photos and videos with the place at which they were made. This annotation is known as geo-tagging.
- 25. Mobile and Wireless Access Networks • Mobile phones are being increasingly used in m-commerce (mobile-commerce). • Short text messages from the mobile are used to authorize payments for food in vending machines, movie tickets, and other small items instead of cash and credit cards. The charge then appears on the mobile phone bill. • When equipped with NFC (Near Field Communication), technology the mobile can act as an RFID smartcard and interact with a nearby reader for payment. • Sensor networks have nodes that gather and relay information they sense about the state of the physical world. • The nodes may be embedded in familiar devices such as cars or phones, or they may be small separate devices. • For example, your car might gather data on its location, speed, vibration, and fuel efficiency from its on-board diagnostic system and upload this information to a database. • One example is tracking the migration of individual zebras by placing a small sensor on each animal. • Also, small birds, rodents()قوارض , and insects can be tracked
- 26. 3- Content Provider Networks(CPN) • Many Internet services are now served from "the cloud," or a data-center network (DCN). • Modern data center networks have millions of servers in a single location. • DCN serve growing demands of cloud computing and are designed to move large amounts of data between servers as well as between the data center and the rest of the Internet. • Data center networks face challenges of scale, both for network throughput ()االنتاجية and for energy usage and Internet. • Main network throughput challenges is "cross-section bandwidth," which is the data rate that can be delivered between any two servers in the network. • Early data-center network designs were based on a simple tree topology, with three layers of switches: access, aggregate()تجميع, and core; this design did not scale well, subject to faults(لألخطاء )عرضة .
- 27. Content Provider Networks (CPN) • Many popular Internet services to deliver content around the world, use a CDN (Content Delivery Network). • CDN is a large collection of servers geographically distributed in such a way that content is placed as close as possible to the users requesting it . • Google, Facebook, and Netflix etc. operate their own CDNs. • Content ranging from static to streaming video, may be replicated in many locations across a single CDN. • When a user requests content, the CDN must decide which replica()نسخة it should serve to that user. • This process must consider the distance from each replica to the client, the load on each CDN server, and traffic load and congestion ()االزدحامon the network itself.
- 28. Content Provider Networks (CPN)
- 30. 4- Transit()عابر Networks • Content and applications are hosted in data-center networks, and we access this content from an access network. • Content traverse Internet from the data center to the access network, and ultimately to our device. • When content provider and your ISP (Internet Service Provider) are not directly connected, they rely on a transit network to carry the traffic between them. • If the network hosting the content and the access network exchange enough traffic between them, they may decide to interconnect directly. • Example of direct interconnection between large ISPs and large content providers, are Google or Netflix. • The ISP and the content provider build and maintain network infrastructure to facilitate interconnecting directly, in many geographic locations. • Transit networks are traditionally called backbone networks.
- 31. 5- Enterprise()مؤسسة Networks Most organizations (e.g., companies, universities) have many computers, normally connected on a common network, allowing employees to share data, information, and compute resources with one another . Resource sharing makes programs, equipment, and especially available to other users on the network , example ,common printer . Most important is sharing information . If all of its computers suddenly went down, a bank could not last more than five minutes .
- 32. Enterprise Networks • Networks called VPNs (Virtual Private Networks) connect the individual networks at different sites into one logical network. • It is an attempt to end the “tyranny طغيانof geography." If user happens to be 15 km away from his data should not prevent him from using it. • In simplest terms, imagine company's information system as one or more databases stored on powerful computers called servers. • These are centrally housed and maintained by a system administrator. • Employees have simpler machines, called clients, with which they access remote data. • The client and server machines are connected by a network.
- 33. Enterprise Networks • Second goal of enterprise computer network has to do with people rather than information. • A computer network can provide a powerful communication medium among employees e.g. email (electronic mail) • Telephone calls may be carried by the computer network instead of by the phone company. • This technology is called IP telephony or VoIP (Voice over IP) when Internet technology is used . • Video with audio, multiple employees at distant locations can see and hear each other as they hold a meeting. • Desktop sharing lets remote workers see and interact with a graphical computer screen. • Third goal is doing business electronically, especially with customers and also suppliers. • Many companies like Airlines, bookstores, and other retailers provide catalogs of their gods and services online
- 34. Network Hardware • Personal area networks (PAN) • Local area networks (LAN) • Home Networks • Metropolitan area networks (MAN) • Wide area networks (WAN) • Internetworks (البينية الشبكات)
- 35. 1-Personal Area Networks(PAN) • PANs (Personal Area Networks) let devices communicate over the range of a Person. • Example, the network that connects your wireless headphones and your watch to your smartphone. • Bluetooth a short-range wireless network to connect these components without wires. • Bluetooth networks use the master-slave paradigm()نموذج as shown. • The system unit (the PC) is master, talking to the mouse or keyboard as slaves. • The master tells slaves what addresses to use, when to transmit, how long to transmit, what frequencies to use. Bluetooth PAN Configuration Bluetooth is a short-range wireless technology standard that is used for exchanging data between fears mobile devices over short distances using UHF radio waves in the ISM bands, from 2.402 GHz to 2.48 GHz, and building personal area
- 37. 2-Local Area Network (LAN) • A LAN (Local Area Network) is a private network that operates within and nearby a single building such as a home or office. • LANs are widely used to connect PC and consumer electronics to share resources (e.g., printers) and exchange information. • Wireless LANs systems, every computer has a radio modem and antenna to communicate with other computers • Each device talks to a device called an AP (Access Point), wireless router, or base station, as shown. • This device relays packets between the wireless computers and also between them and the Internet, • In mesh network configuration, nearby devices relaying packets for one another. • Relays may Be same nodes as the endpoints; or a separate collection of nodes whose sole responsibility is relaying traffic. • WIFI a popular standard for wireless LANs called IEEE 802.11.
- 39. Local Area Network (LAN) • Wired LANs use many different transmission technologies like copper, coaxial cable, and optical fiber. • LANs have limited size, the worst-case transmission time is bounded and known. • Wired LANs can run at speeds ranging from 100 Mbps to 40 Gbps. • They have low latency (never more than tens of milliseconds) and infrequent transmission errors and higher throughput than wireless LANs. • IEEE 802.3, called Ethernet, is most common type of wired LAN. • Fig shows an example switched Ethernet topology. • Each device speaks Ethernet protocol and connects to a device called switch with a point-to-point link • Switch relays packets between computers that are attached to it, using address in each packet to determine which computer to send. • A switch has multiple ports, to connect to computer or another switch. • To build larger LANS, switches are plugged into each other using their ports.
- 40. • What happens if you plug them together in a loop? Will the network still work? • All switches now use her anti-looping algorithm • Protocol will decide what paths packets should travel to reach intended computer. • It is possible to divide one large physical LAN into two smaller logical LANs. • Example, the engineering and finance departments of a company each can have its own network VLAN (Virtual LAN) • In this design, each port is tagged with a “color,” say green for engineering and red for finance. • The switch will forward packets accordingly. • Broadcast packets sent on a red port, will not be received on a green port.
- 41. Local Area Network (LAN) Ethernet design broadcasts all packets over a single linear cable . Switched Ethernet (classic Ethernet) uses a simple algorithm: computers could transmit whenever the cable was idle ( .)عاطل If two of more packets collided , اصطدمت each computer waited a random time and try later . Both wireless and wired broadcast LANS can allocate خصص resources statically or dynamically . A typical static allocation will divide time into discrete intervals and use a round-robin algorithm, allowing each machine to broadcast only when its time slot comes up Static allocation wastes channel capacity, when a machine has nothing to transmit or receive during its allocated slot . So, Dynamic allocation methods for common channel are used which can be either centralized or decentralized In centralized, there is a single entity, for example, the base station in cellular networks, which determines who goes next. It might do so by accepting multiple packets and prioritizing them according to some internal algorithm . In decentralized channel allocation method, no central entity; each machine must decide for itself whether to transmit
- 42. Home Network • Home networks are a type of LAN; they may have a broad, diverse range of Internet-connected devices, and must be particularly easy to manage, dependable, and secure, especially in the hands of non-technical users. • Many years ago, a home network would probably have consisted of a few laptops .Today, a home network may include devices such as smartphones, wireless printers, thermostats, TV and so on. • This huge scale and diversity تنوعof Internet-connected devices introduces new challenges for designing, managing, and securing a home network. • Although the home network is just another LAN, in practice it is likely to have different properties than other LANs, for several reasons. • First, the devices that people connect to their home network need to be easy to install and maintain. • The devices need to be foolproof and work without requiring the user to read and fully understand a 50-page manual. • Second, security and reliability have higher stakes because insecurity of the de- vices may introduce direct threats to consumer health and safety.
- 43. Home Network • Third, home networks evolve تتطور organically, as people buy various consumer electronics devices and connect them to the network. • As a result, in contrast to a more homogeneous enterprise LAN, the set of technologies connected to the home network may be significantly more diverse. • Home networks typically operate over wireless networks. • Relianceاالعتماد on wireless networks in the home, however, does introduce unique performance and security challenges. • First, as users exchange more traffic on their home networks and connect more devices to them, the home wireless network is increasingly becoming a performance bottleneck. • Second, wireless radio waves can travel through walls (in the popular 2.4 GHz band, but less so at 5 GHz). • Power-line networks can also let devices that plug into outlets broadcast information throughout the house.
- 44. Metropolitan Area Network (MAN) • A MAN (Metropolitan Area Network) covers a city. • Example, the cable television networks. • Earlier a large antenna was placed on top of a nearby hill and a signal was then piped to the subscribers’ houses. • After Internet cable TV network operators started providing two-way Internet service in unused parts of the spectrum. • MAN might look something like the system shown in Fig. • In Figure, both television signals and Internet being fed into the centralized cable head-end, for distribution to people's homes.
- 46. Wide Area Network (WAN) • WAN (Wide Area Network) spans a large geographical area, often a country, a continent, or even multiple continents. • AWAN may serve a private organization (enterprise WAN), or it may be a commercial service offering (transit network) • Example of Wired WANs, company with branch offices in different cities Perth, Melbourne, and Brisbane. • Each of these offices contains computers as hosts for running programs (i.e., application). • The rest of the network that connects these hosts s communication subnet, or just subnet. • The subnet carries messages from host to host. • Subnet consists of two distinct components: transmission lines and switching elements. • Transmission lines move bits between machines. • They can be made of copper wire, coaxial cable, optical fiber, or radio links. Often organizations use the lines from a telecommunications company.
- 49. Wide Area Network (WAN) • Switching elements, or switches, are specialized devices that connect two or more transmission lines. • When data arrive on an incoming line, the switching element decides an outgoing line to forward them. • These switching element are routers. • In most WANS, the network contains many transmission lines, each connecting a pair of routers, • Two Routers that do not share a transmission line must do so via other routers. • There may be many paths that connect these two routers. • Network uses routing algorithm to decide which path to use. • Router uses forwarding algorithm to decide where to send a packet next.
- 50. • Fig. shows virtual private network. • In contrast to a network with dedicated physical links, a VPN provides virtualization, i.e. flexible reuse of a resource (Internet connectivity). • With a VPN, performance may vary with that of the underlying Internet connectivity. • The network itself may also be operated by a commercial Internet service provider (ISP) • Fig. shows this structure, which connects the WAN sites to each other, as well as to the rest of the Internet. • In satellite systems (using WANs wireless technologies), each computer on the ground has an antenna through which • it can exchange data with a satellite in orbit. Wide Area Network (WAN)
- 52. Wide Area Network (WAN) • The cellular telephone network is another example of a WAN that uses wireless technology. • This system has already gone through five generations. • The first generation was analog and for voice only. • The second generation was digital and for voice only. • The third generation is digital and is for both voice and data. • The fourth generation is purely digital, even for voice.
- 53. • Each cellular base station covers a distance much larger than a wireless LAN. • The base stations are connected to each other by a backbone network that is usually wired. • The data rates of cellular networks are much smaller than a wireless LAN that can range up to on the order of 7 Gbps. • More recently, organizations distributed across geographic regions and need to connect sites are designing and • deploying software-defined WANs or SD-WANs, which use different, complementary technologies to connect disjoint • sites but provide a single SLA (Service-Level Agreement) across the network. • SD-WANs are one example of an SDN (Software-Defined Network), a technology that control the network using a combination of programmable switches with control logic implemented as a separate software program.
- 55. Internetworks(Internet) • A collection of interconnected different networks is called an internetwork or internet. • Not the global Internet (which is one specific internet). • The Internet connects content providers, access networks, enterprise networks, home networks, to one another. • A network comprises the combination of a subnet and its hosts. • A subnet might be described as a network, as “ISP network”. • An internetwork might also be described as a network, as in the case of the WAN. • An internet involves the interconnection of distinct, independently operated networks. • The device that makes a connection between two or more networks and provides the necessary translation, both in terms of hardware and software, is a gateway . • Gateways are distinguished by the layer at which they operate in the protocol hierarchy.
- 59. Network Software • Protocol hierarchies • Design issues for the layers • Connection-oriented versus connectionless service • Service primitives • Relationship of services to protocols
- 60. Network Software Protocol Hierarchies Layers, protocols, and interfaces.
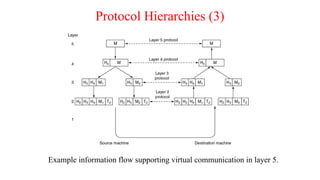
- 62. Protocol Hierarchies (3) Example information flow supporting virtual communication in layer 5.
- 63. Connection-Oriented Versus Connectionless Service • Layers can offer two different types of service to the layers above them: connection-oriented and connection less. • Connection-oriented service is modeled after the telephone system. • To use connection-oriented network service, the service user first establishes a connection, uses the connection, and then releases the connection. The essential aspect of a connection is that it acts like a tube: the sender pushes objects (bits) in at one end, and the receiver takes them out at the other end in the same order.
- 64. Connection-Oriented and Connectionless Services Six different types of service.
- 65. Reference Models • OSI reference model • TCP/IP reference model • Model used for this text • Comparison of OSI and TCP/IP • Critique of OSI model and protocols • Critique of TCP/IP model
- 66. Principles for the seven layers • Layers created for different abstractions. • Each layer performs well-defined function. • Function of layer chosen with definition of international standard protocols in mind. • Minimize information flow across interfaces between boundaries. • Number of layers optimum .
- 70. Design Issues for the Layers • Addressing • Error Control • Flow Control • Multiplexing • Routing
- 71. Service Primitives Five service primitives for implementing a simple connection- oriented service.
- 72. Service Primitives (2) Packets sent in a simple client-server interaction on a connection-oriented network.
- 73. Services to Protocols Relationship The relationship between a service and a protocol.
- 74. Example Networks • The Internet • Connection-Oriented Networks: X.25, Frame Relay, and ATM • Ethernet • Wireless LANs: 802:11
- 75. Internet Usage Traditional applications (1970 – 1990) • E-mail • News • Remote login • File transfer
- 76. Architecture of the Internet Overview of the Internet.
- 77. Ethernet Architecture of the original Ethernet.
- 78. Wireless LANs (a) Wireless networking with a base station. (b) Ad hoc networking.
- 79. Wireless LANs (2) The range of a single radio may not cover the entire system.
- 80. Network Standardization • Who’s Who in the Telecommunications World • Who’s Who in the International Standards World • Who’s Who in the Internet Standards World
- 81. IEEE 802 Standards The 802 working groups. The important ones are marked with *. The ones marked with are hibernating. The one marked with † gave up.
- 82. Metric Units The principal metric prefixes.
Editor's Notes
- #3: Video lectures : https://www.youtube.com/watch?v=YjPBbblHCZw&list=PL9P1J9q3_9fMNkawVIs9wEk3Kk2IcqNK0 https://www.youtube.com/watch?v=whMHiWSqorQ&list=PL1FYvHNDcUxnNRtratNcpQAU2Rw5DDJY2&index=2
- #29: https://www.dnsstuff.com/network-throughput-bandwidth