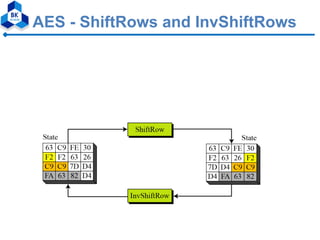
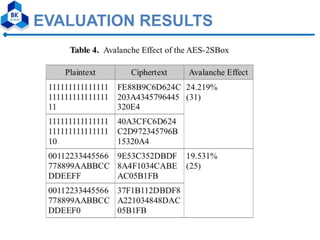
The document proposes a modified AES algorithm using multiple substitution boxes (S-Boxes) to improve performance. It describes the standard AES algorithm and then proposes modifications. Specifically, it suggests using two S-Boxes - the original Rijndael S-Box along with a new S-Box constructed by XORing each value of the original S-Box with 7F and applying an affine transformation. Evaluation results showed that the modified algorithm with two S-Boxes improved speed performance compared to standard AES, while slightly weakening security. The modified algorithm is also more efficient to implement using low-cost processors and minimal memory.
































![AES -Key Expansion submodule
• RotWord performs a one byte circular left shift on a word
For example:
RotWord[b0,b1,b2,b3] = [b1,b2,b3,b0]
• SubWord performs a byte substitution on each byte of
input word using the S-box
• SubWord(RotWord(temp)) is XORed with RCon[j] – the
round constant](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-34-320.jpg)



![AES - CONSTRUCTION OF THE NEW S-BOX
vThe second S-Box is derived from the
original S- Box as designed in the AES
ØExclusive OR Operation
§ each cell in the AES-Rijndael will be
XORed with 7F
AES-Rijndael[x,y] XOR (7F)
§ The Key[i] shall be any hexadecimal value
between 00 to FF (Table 1. AES-
2SboxXOR7F)](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-38-320.jpg)







![Referents
• [1] National Institute of Standards and
Technology, Advanced Encryption Standard,
FIPS 197 (2011).
• [2] Paper “Modified AES Algorithm Using
Multiple S-Boxes”
• [3] Wiki & slide & Internet.
50](https://image.slidesharecdn.com/modifiedaesalgorithmusingmultiples-boxes-190630144613/85/Modified-aes-algorithm-using-multiple-s-boxes-47-320.jpg)
